Nebula : flag00
Hey, guys i just decided to solve the Nebula machine from exploit education.
I’ve also made a youtube video about it which you can refer to.
Youtube link : https://youtu.be/9Xd28FjugM8
Blog : https://blankdash.wordpress.com/2020/02/18/nebula-walkthrough-exploit-level00/
nebula is a vulnurable VM that teaches a variety of common (and less than common) weaknesses and vulnerabilities in Linux. Below listed are some of the things that we would be able to learn.
- SUID files
- Permissions
- Race conditions
- Shell meta-variables
- $PATH weaknesses
- Scripting language weaknesses
- Binary compilation failures
At the end of Nebula, the user will have a reasonably thorough understanding of local attacks against Linux systems, and a cursory look at some of the remote attacks that are possible.
So lets get started, Download the image from here the above give url and mount it on your VM. The username and passwords are as given below for the VM.

Username: nebula
Password: nebula
Navigate to level00, the task for the level00 is to run a executable file thats located somewhere on the filesystem. Inorder to do that we will use the find command.
As always manual pages would help, “man find”.
Login to the VM using the uname and password : nebula
once logged in, lets try using the find command to locate to the file.
Since this file a Set UID program, it would have a executable permission. Lets try finding all executable files in the system.
$ find / -perm 4000
You can see this would return in a lot of errors since, we do not have permission to access the entire file system.

errors
Now lets try to redirect all of the errors to a different place in the filesystem which we have access to, in most cases temperory storage spaces like “/dev/null”, “/dev/shm”, “/tmp/” would be a good choice to redirect errors. Inorder to redirect errors you should be familiar with standin, standout and errors in the file system.
Stanin – is represented by 0
standout – is represented by 1
Errors – are represented by 2
Thus running the below command will redirect all errors to a different place, allowing us only to view the results.
$ find / -perm 4000 2>/dev/null

redirect errors
This leaves us with nothing, since we do not have an exact match. We could find partial matches for the file permissions in the system.
$ find / -perm -4000 2>/dev/null


results
We do have a lot of results, what we can do is to pipe the output to more and look at all the results or something similar, but we do know that its named “flag00” so i could grep for all results that contain the name “flag00”
$ find / -perm -4000 2>/dev/null | grep flag00
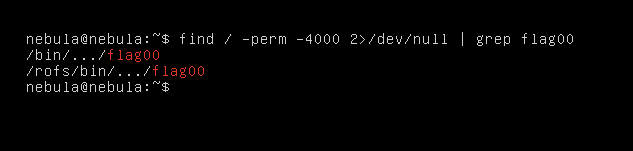
filter for flag
We have a couple of results, lets take a look into the “/bin/…/flag00”
“…” – here is a directory.
$ cd /bin/…/
$ ls -la
$ ./flag00

execute file
so we get an error, looking at the challenge, we do know that we have to login as “level00” with a password “level00” to execute the file. Lets try doing that.
$ su level00
$ cd /bin/…/
$ ./flag00
we might have to run “getflag” to complete the challenge
$ getflag
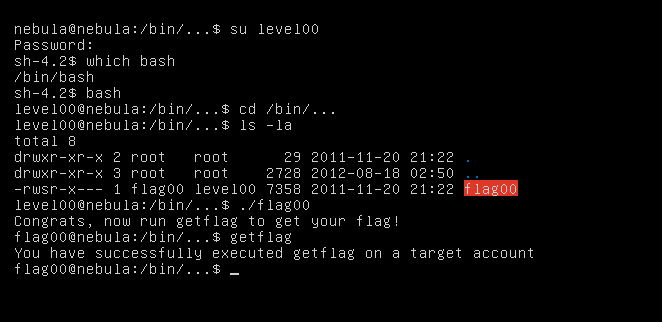
getflag
Thats it for level00, hope you have learnt something. Ill come up with another post for the next level.
Later.
-blankdash

Comments