About Ensiko
This malware is a threat to any system using PHP. It can be used remotely by someone to carry on malicious activities. It is capable of executing shell level (OS) commands and send it back to remote executioner. It also scans systems and servers for particularly sensitive or valuable information.
Few Technical Details
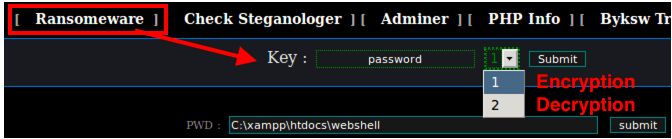
- The malware can be password-protected.
- The file-encryption component is one of the capabilities that can be used to wage attacks against servers.
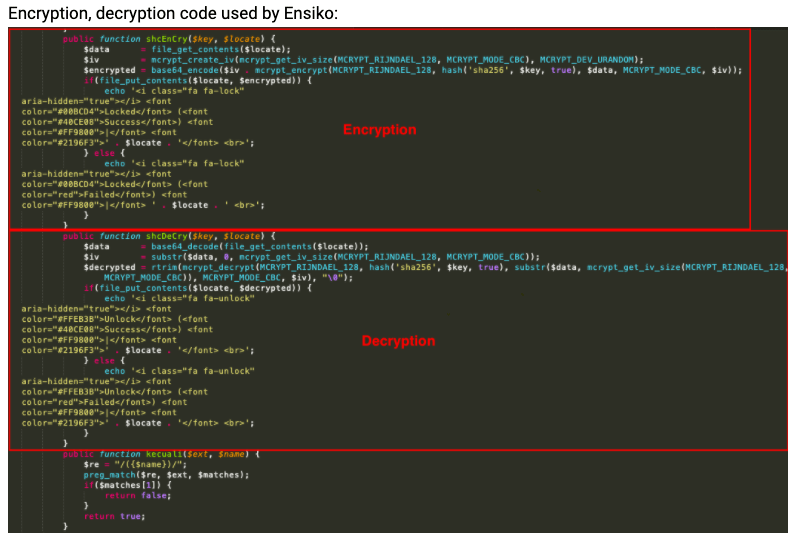
- According to the researchers at Trend Micro, the malware uses PHP RIJNDAEL_128 algorithm with CBC mode to encrypt files in a web shell directory.
- Another function includes the recursive overwrite of all files with a specified extension in a directory of a web shell.
What Are Researchers Saying ?
Ensiko is a PHP WebShell that can affect Windows, macOS and Linux systems. Trend Micro analyst Aliakbar Zahravi explains how the newly-discovered malware can remotely control the system and infect the machine.
Security researchers at Trend Micro reported a new malware with a host of capabilities including remote server control and encryption. Dubbed Ensiko, the malware is a WebShell security threat, capable of performing malicious activities at the behest of its operator.
Aliakbar Zahravi, Malware Analyst at Trend Micro wrote in a blog that Ensiko is written in PHP and can victimize any internet-facing server or system running on an environment that supports PHP. This makes Windows, macOS as well as Linux susceptible to Ensiko attacks. As is the case with typical WebShell, Ensiko can execute code and scripts to gain remote server administration and control.
Once a system is infected, Ensiko can exhibit ransomware capabilities by encrypting stored files. It implements PHP RIJNDAEL_128 with block cipher mode of operation to encrypt files.
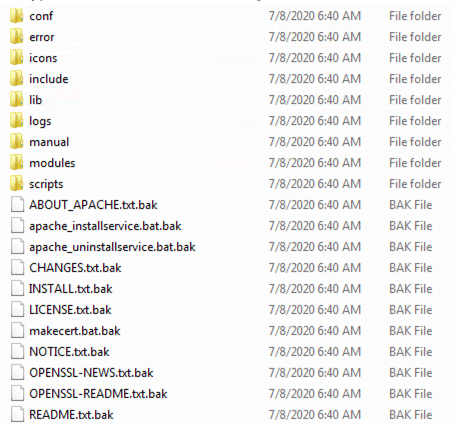
Once encrypted, the malware, now acting as a ransomware, attaches files with .bak extension.
Malicious Capabilities
Ensiko’s malicious capabilities can also be misused to disrupt services like website defacing, exfiltrate and disclose sensitive server data. It can also be used to carry out brute-force attacks against file transfer protocol (FTP), cPanel, and Telnet.
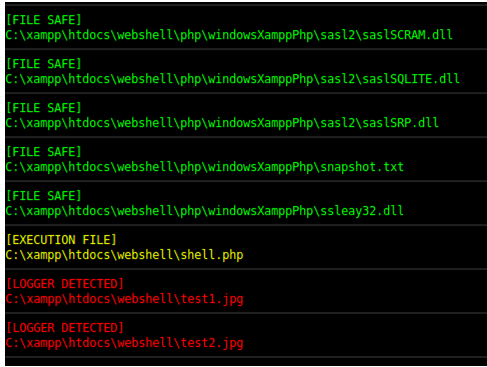
A threat actor can potentially load additional tools for malicious activity from the Pastebin, which it stores in tools_ensikology. Furthermore, an image file’s EXIF data headers are leveraged for hiding and later extracting code using the Steganologer function. Zahravi illustrates this with the image below.
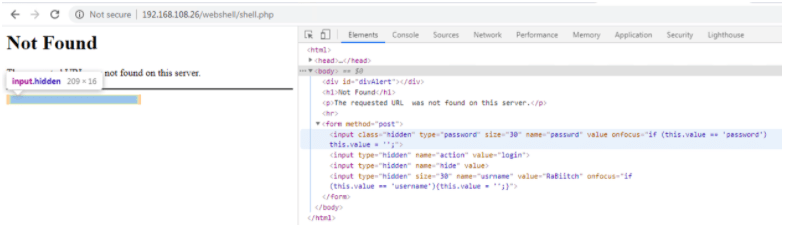
Password Protected Malware ??
One of the unconventional characteristics of Ensiko is that it can be password protected for authentication. It also incorporates a hidden input form for login as shown below.

Comments