Delivering maximum value is a momentous challenge for cybersecurity organizations. It takes a decisive effort to organize and prioritize the proper goals that are meaningful to the business, and establish operational excellence to deliver effectiveness and efficiency. But running a good risk program that manages the defensive posture by addressing internal vulnerabilities is not enough. There are external factors that have a profound impact on the likelihood of attack and business factors that matter to the executive suite which could represent a competitive advantage to the corporate bottom line.
Here are my 3 tips to strategically enhance a cybersecurity team’s long-term value-proposition to the organization.
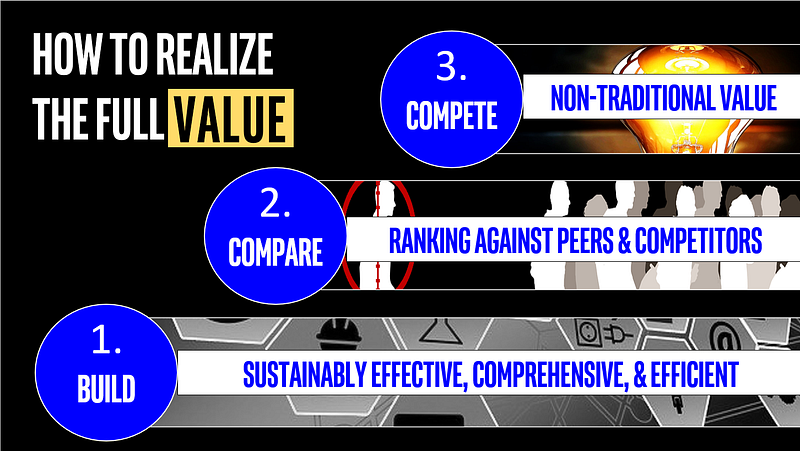
It comes down to three tiers of progress. Build, Compare, and Compete.
First, we must build a sustainably effective, comprehensive, and highly efficient cybersecurity capability. This is the most important step that every cybersecurity leader works towards on a daily basis.
Although the core of this work is fundamental to our operational existence, we need to pay attention to aspects often ignored, including the concept of aligning efficiency to financial optimizations and disproportionate resource allocation weighted to the most likely attacks. It is also crucial to see cybersecurity as a never-ending endeavor that must be incorporated into the overall everyday business processes and goals.
Sustainability is another key objective that is often overlooked while distracted by short-term battles. CISOs must plan for financial constraints, evolving threats, shifting technology landscapes, confusing regulations, and rising expectations of security to ensure longevity. Cybersecurity cannot continue to impose ever greater expense, friction, and frustration on the organization. A breaking point will be reached if proper strategic planning is not employed.
Second, and this is where we diverge from what most CISOs focus upon, is about Comparing your organization to others in your sector. We must understand the attacker’s perspective. When they look for their next victim, they are evaluating who is best to target. By looking at your organization in contrast to others, you can understand how you appear in the landscape, and if you are in the pack or falling behind. You don’t want to be the easy prey.
Third, cybersecurity in operations, products, and services is becoming a Competitive advantage in many fields. The expectation of digital security, privacy, and safety, is rising as a purchase and loyalty factor with consumers. This is where cybersecurity can help the organization compete and therefore contribute to fulfilling the business goals (like revenue, market share, upselling, and more).
Cybersecurity can be a differentiating factor in many ways, including non-traditional competition. Savvy companies like Apple and Microsoft are maneuvering to improve their bottom line! Cybersecurity has the opportunity to not only enable, but contribute to corporate goals. Explore the potential and align as necessary to deliver value in new ways!
Those are my 3 high-level tips to maximize cybersecurity value. By achieving success in these domains, you will be far ahead of others in being able to communicate sustainability and value for your cybersecurity program.
Drop me a note if you need help or have questions. To learn more in-depth about each area, subscribe to my Cybersecurity Insights channel where I will be posting videos and interviews that detail the challenges and best practices.

Comments