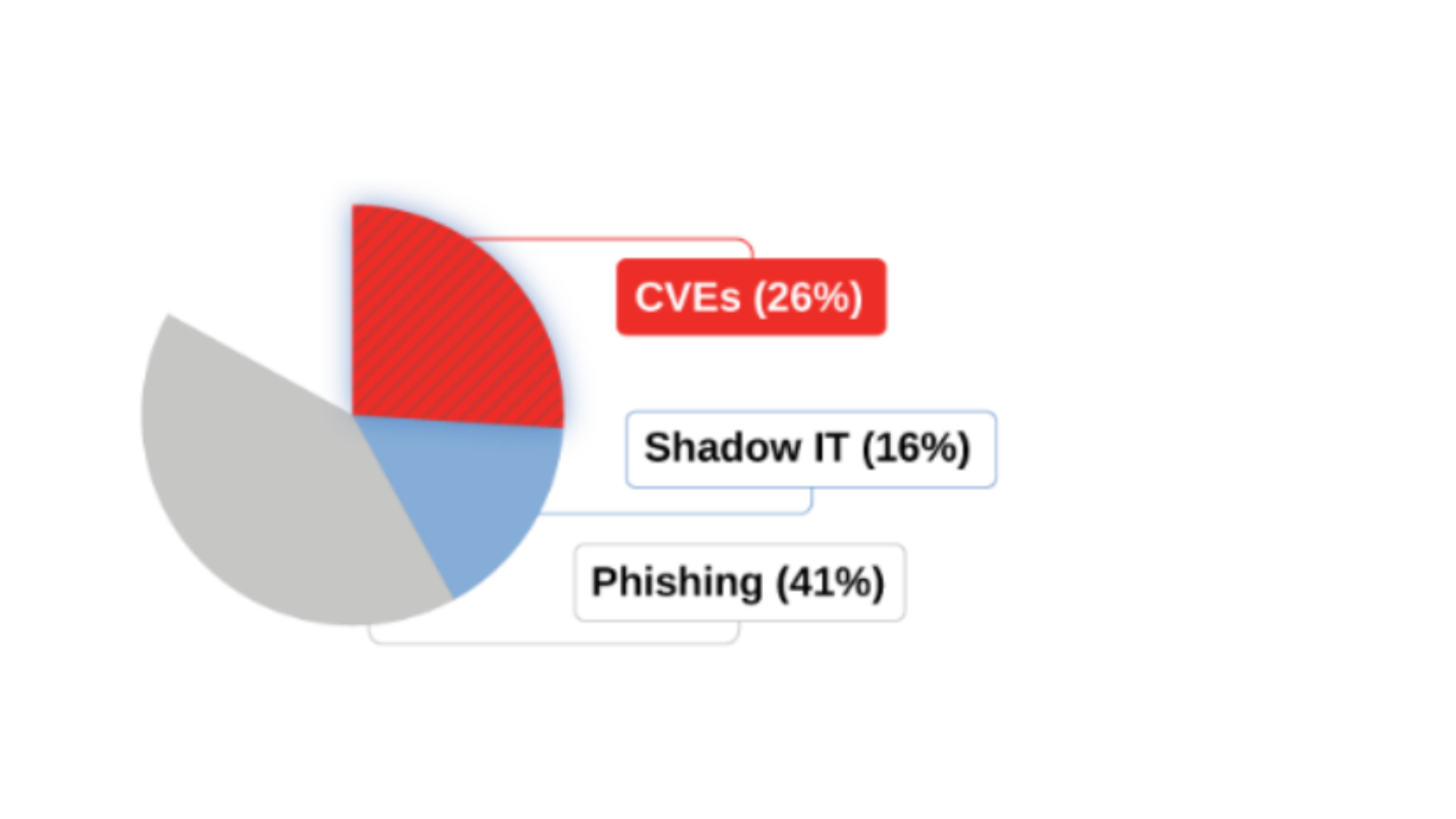
According to latest Threat Intelligence, 80% of the times, Ransomware gets initial access using Top 3 Attack Vectors:
1. Exploiting Vulnerabilities
2. Shadow IT & Stolen Credentials
3. Various Variants Of Phishing Attacks
This webinar covers 6 most critical and ransomware weaponized CVEs published in the last 3 months and how CISOs can identify them and immediately decrease the chance of Ransomware by 26%.
Key Discussion Points :
- Key Insights on Reducing Ransomware Risk by 26%
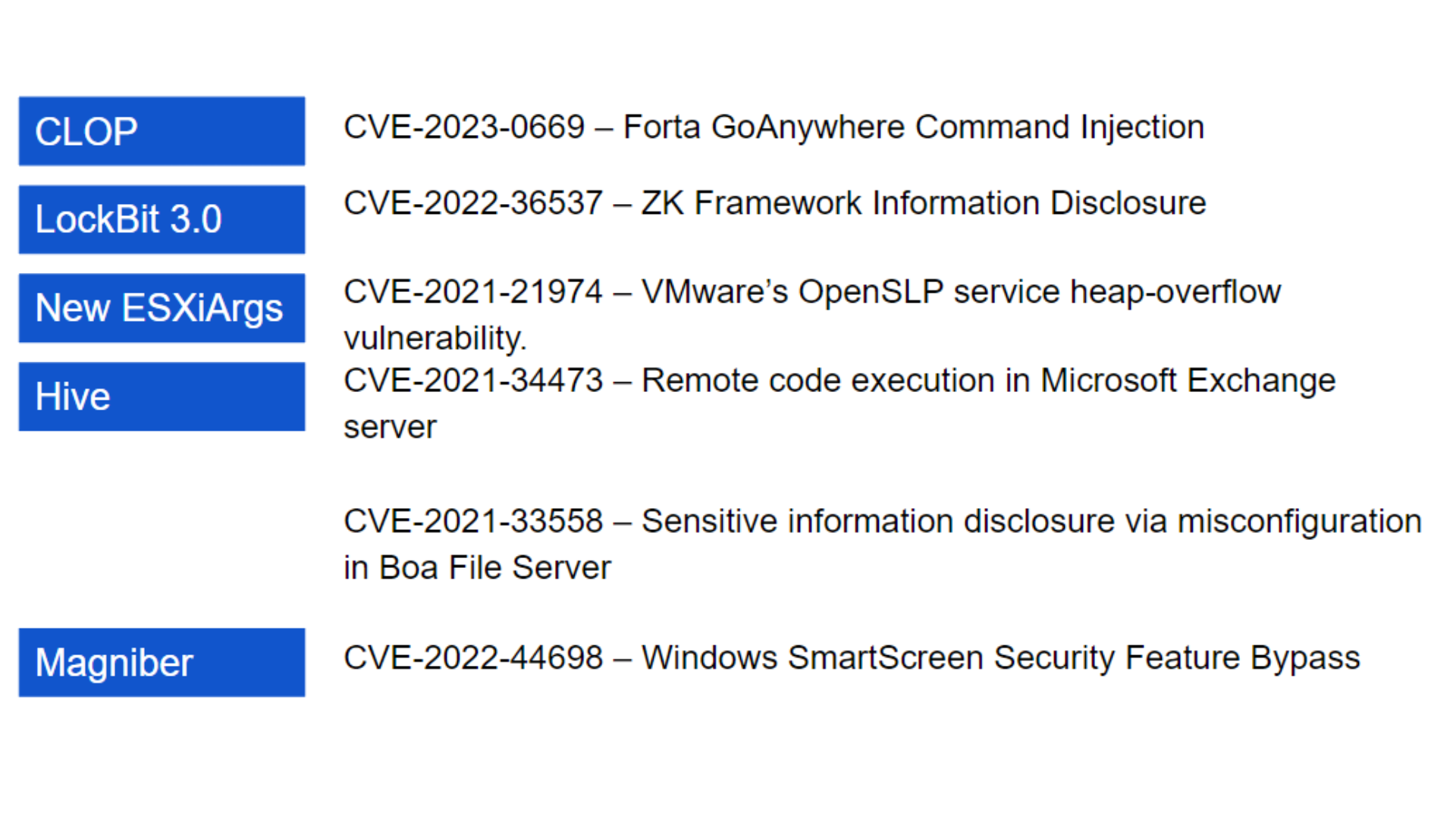
- Top 6 CVEs in last 3 months tracked by FireCompass Research Team
- Key Recommendations and Best Practices
- Know the 3 Weaknesses which leads to 80% Ransomwares
About Speaker
Jitendra Chauhan, Head of Research at FireCompass. Jitendra holds multiple patents in Information Security and has 18+ years of experience in key areas such as Building and Managing Highly Scalable Platforms, Red Teaming, Penetration Testing and SIEM.
(Webinar) Recorded
Discussion Highlights
1. 3 Weaknesses leads to 80% Ransomewares
2. Attackers Capability to scan internet in few days
One of the typical automation, without any human intervention is following
- Scan for targets on mass scale
- Profile the targets using custom crawlers or fingerprinting techniques
- Detect CVEs based on technology, or banner
- Attempt exploitation
- Attempt persistence
3. Ransomewares runs on Global Attack Surface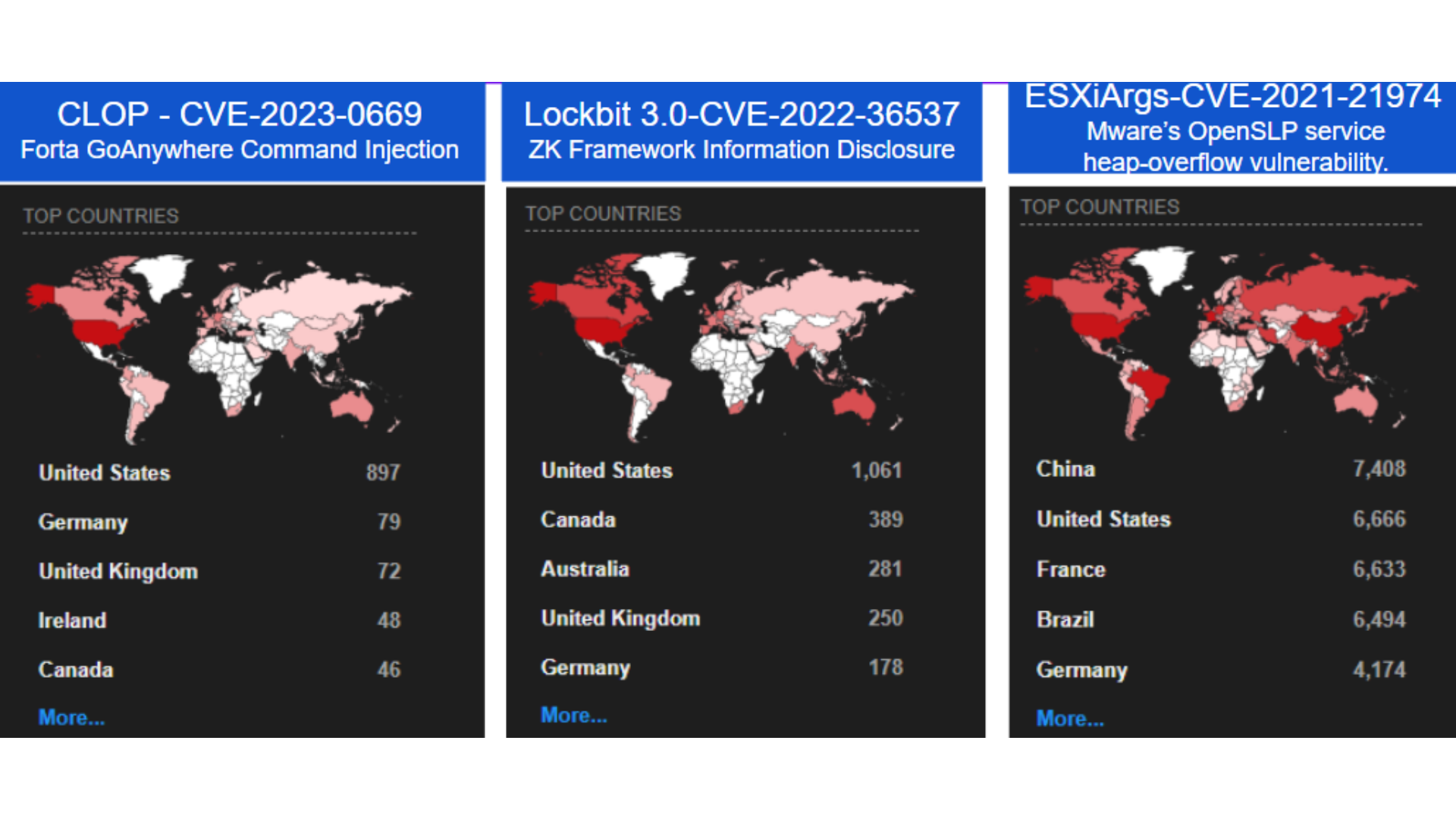
.png?profile=RESIZE_710x)
4. CVE Prioritized in April by Firecompass
5. Possible Recommendations
- Threat Intel + Pentesting on Daily Basis.
- Combine ASM + Threat Intel + Vulnerability Management.
- Firecompass Day 1 CVE + Threat Exposure Alerts
6. Ransomewares targetted CVEs


Comments