This webinar covers various aspects, including the rise in cyber security incidents, identification of vulnerabilities and loopholes, effective prevention strategies, mitigation techniques, and more. It aims to provide a comprehensive understanding of the evolving cybersecurity landscape in the context of Web3 technologies.
Key Discussion Points
- Discuss Security Incidents & Business Use Case
- Understanding Web 3 Pros
- Understanding Web 3 Cons. Prevention mechanism
- How to make sure that it doesn’t happen to you?
About Speaker
Gregory Pickett is a Blackhat USA Speaker, CISSP, GCIA, GPEN. He is the founder and Head of Cybersecurity Operations for Hellfire Security. He has presented research at over seventeen international conferences. He is a Six-time speaker at Defcon and three-time speaker at Blackhat.
(Webinar) Recorded
Discussion Highlights
1. Common Attacks
- Price Oracle Manipulation
- Improper Access Control
- Improper Validation and Logic Errors
- MEV Attacks (Front Running, Sandwiches)
- Traditional Methods :
SIM Swapping, Phishing Attacks, Vulnerable Nodes, Abused Permissions, Abused Network
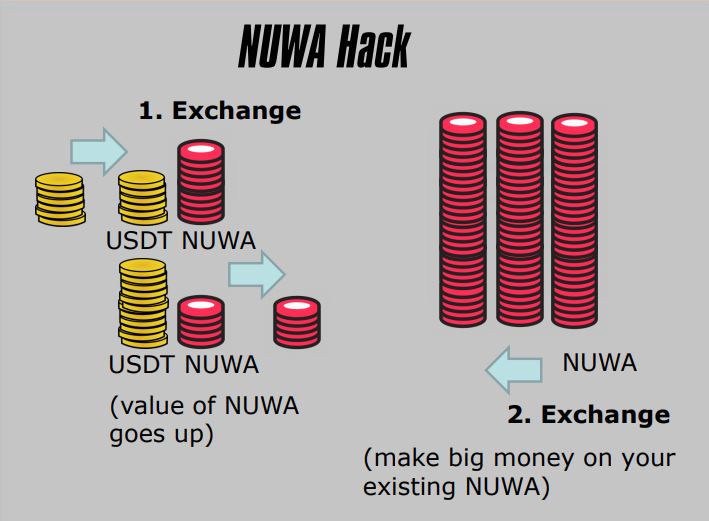
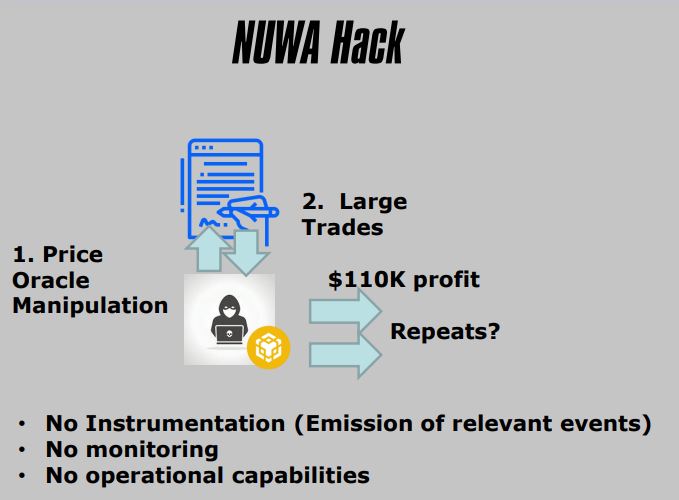
2. NUWA Hack
- ERC-20 Token
- Price Oracle Manipulation
- Publicly Known
- Liquidity Pool Imbalance
- Distorted Exchange Rate
- Used to Exchange At A Favorable Rate
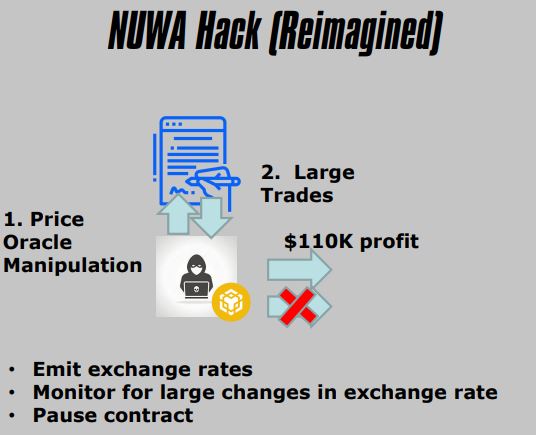
3. Important Events/States To Emit
- Low Balances
- Liquidity Pool Ratios (Or Exchange Rates)
- Change in Ownership
- Funds Distributions
- Attributes Generated
- Wins/Losses
4. Important Operational Capabilities
- Blacklist Wallets
- Transfer Pools
- Pause Contract
- Kill Contract
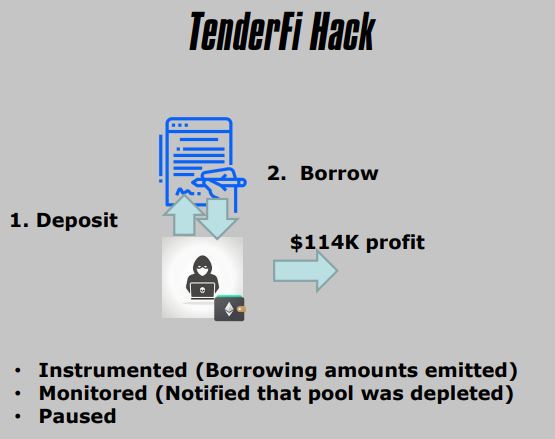
5. TenderFi Hack
- DeFi Platform
- Price Oracle Misconfiguration
- Publicly Known
- Implicit Decimal Point
- Overvalued Token
- Produced a very favorable loan (larger than total value of all Bitcoin)
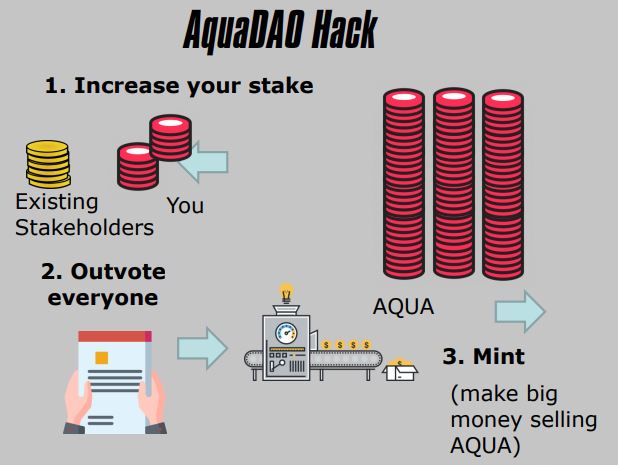
6. AquaDAO Hack
- Decentralized Autonomous Organization
- Governance Attack
- Insufficient Stake
- Malicious Proposal
- Destroyed Value
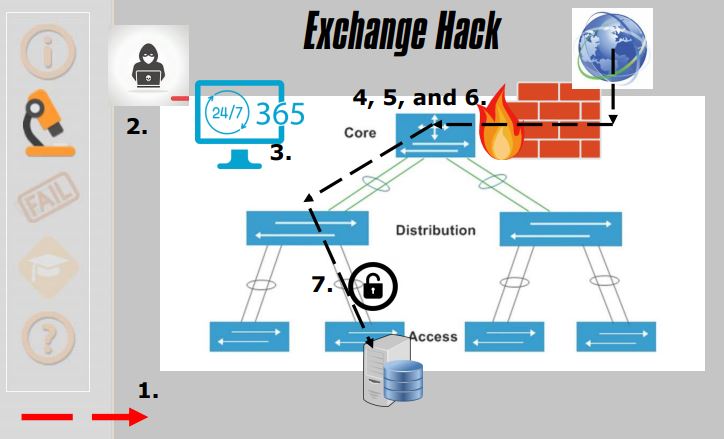
7. Exchange Hack
- Hot Wallet
- Abused Privileges
- Not Public
- No Privileged Access Management
- No Compensating Controls
- Transferred Funds Out of Hot Wallet
- Drained Hot Wallet
- No Privileged Access Management
- No Log Aggregation
- No Monitoring of Login/Logout Events
- No Access Attestation
- Enterprise Network
- Abused Network
- Not Public
- No Zoning, No Hardening, and No Governance
- No Compensating Controls
- All Customer Data include OTP Seeds
- Wouldn’t you like to know
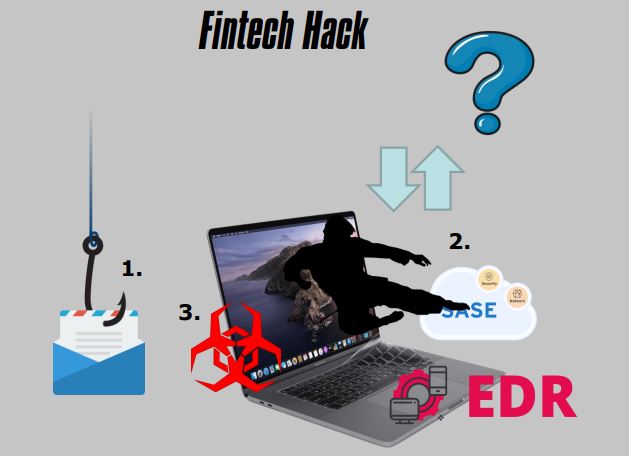
8. Fintech Hack
- Key Engineer
- Phishing Attack
- Not Public
- Lacking Cybersecurity Fundamentals
- Buying Products to Solve Problems
- Who Knows
- No Security Awareness Training
- No SIEM Tuning
- No Flow Monitoring
- No Privileged Access Management
9. Buying Products (or Services) to Solve Problems
- Protecting Users (EDR)
- Protecting Network (SASE)
- Monitoring Activity (SIEM)
- Secure Software (SSDLC) (Audit Services)
10. Hope Is Not A Strategy
- They Are Looking for the Perfect Products
- If we have the right X/Y/Z, we will never have to worry about threats
- Web3 Itself Is Seen In A Similar Fashion
- Just Perform More Audits
(PPT) Presentation From The Discussion


Comments