Executive Summary
The cybersecurity threat landscape around July 13, 2025, revealed significant security developments across critical infrastructure and enterprise environments. Key developments include Microsoft's substantial Patch Tuesday addressing 130 vulnerabilities, CISA's urgent addition of Citrix NetScaler CVE-2025-5777 to the Known Exploited Vulnerabilities catalog, and the Ingram Micro ransomware attack disrupting global IT supply chains. Organizations must prioritize immediate defensive measures while maintaining strategic security posture alignment with current threat intelligence indicators.
Key Breach Incidents Overview
- Microsoft Patches 130 Vulnerabilities Including Critical SPNEGO and SQL Server Flaws - Multiple Sources
- CISA Adds Citrix NetScaler CVE-2025-5777 to KEV Catalog as Active Exploits Target Enterprises - TheHackerNews
- Ingram Micro Confirms Ransomware Attack After Days of Downtime - CSO Magazine
- CISA Releases Thirteen Industrial Control Systems Advisories - CISA Alerts & Advisories
- UK Arrests in 'Scattered Spider' Ransom Group - Krebs on Security
- Multiple Critical Vulnerabilities Added to NIST NVD - National Vulnerability Database
- Qantas Data Breach Affects 5.7 Million Customers - Infosecurity Magazine
- Nova Scotia Power Ransomware Attack Impacts Billing Systems - Cybersecurity Insiders
Major Incident Analysis
Microsoft Patches 130 Vulnerabilities Including Critical SPNEGO and SQL Server Flaws
Source: Multiple Sources

Timeline: July 8, 2025 - Microsoft released comprehensive security updates
Attack Vector: Multiple vectors including network-based exploitation, authentication bypass, and memory corruption
Threat Actor: Various threat actors targeting unpatched systems
CVE References:
- CVE-2025-49719: SQL Server Information Disclosure (CVSS 7.5) - Publicly disclosed vulnerability affecting SQL Server 2016-2022
- CVE-2025-47981: SPNEGO Extended Negotiation RCE (CVSS 9.8) - Critical pre-authentication vulnerability
- CVE-2025-49735: Windows KDC Proxy Service RCE (CVSS 8.1) - Pre-auth remote compromise risk
- CVE-2025-49695-49697: Microsoft Office RCE vulnerabilities (CVSS 8.4)
- CVE-2025-49740: Microsoft Defender SmartScreen Bypass (CVSS 8.8)
MITRE ATT&CK Mapping:
- T1190 (Exploit Public-Facing Application): Exploitation of unpatched vulnerabilities
- T1068 (Exploitation for Privilege Escalation): Local privilege escalation through various flaws
- T1055 (Process Injection): Potential code execution through memory corruption
Analysis: This Patch Tuesday represents one of the most significant security updates of 2025, addressing 130 vulnerabilities with 14 rated as critical. The SPNEGO vulnerability (CVE-2025-47981) is particularly concerning due to its "wormable" potential, reminiscent of WannaCry-level threats. The SQL Server information disclosure flaw affects a broad range of versions and could expose cryptographic keys. Organizations must prioritize rapid deployment of these patches, especially for internet-facing systems.
CISA Adds Citrix NetScaler CVE-2025-5777 to KEV Catalog as Active Exploits Target Enterprises
Source: TheHackerNews
Timeline: July 11, 2025 - CISA added to KEV catalog; exploitation began mid-June 2025
Attack Vector: Authentication bypass through insufficient input validation in Gateway/AAA configurations
Threat Actor: Multiple threat actors including RansomHub-affiliated groups
Indicators of Compromise (IOCs):
- Suspicious requests to
/p/u/doAuthentication.doendpoints - Unexpected XML data in responses containing
<InitialValue>fields - Memory overread patterns in ns.log files
CVE References:
- CVE-2025-5777: Citrix NetScaler Out-of-Bounds Read (CVSS 9.3) - Authentication bypass vulnerability
- CVE-2025-6543: Related NetScaler Buffer Overflow (CVSS 9.2) - Also under active exploitation
MITRE ATT&CK Mapping:
- T1190 (Exploit Public-Facing Application): Direct exploitation of internet-facing NetScaler appliances
- T1078 (Valid Accounts): Session token theft for unauthorized access
- T1021 (Remote Services): Lateral movement through compromised VPN/proxy access
Analysis: The "Citrix Bleed 2" vulnerability represents a critical threat to enterprise networks, with CISA issuing an unprecedented 24-hour patching deadline. Active exploitation by 10 unique IP addresses across multiple countries targets organizations in the US, France, Germany, India, and Italy. The vulnerability allows memory bleeding of sensitive session tokens, enabling unauthorized access to internal applications and networks. Organizations must immediately upgrade to version 14.1-43.56 or later and terminate all active sessions.
Ingram Micro Confirms Ransomware Attack After Days of Downtime
Source: CSO Magazine
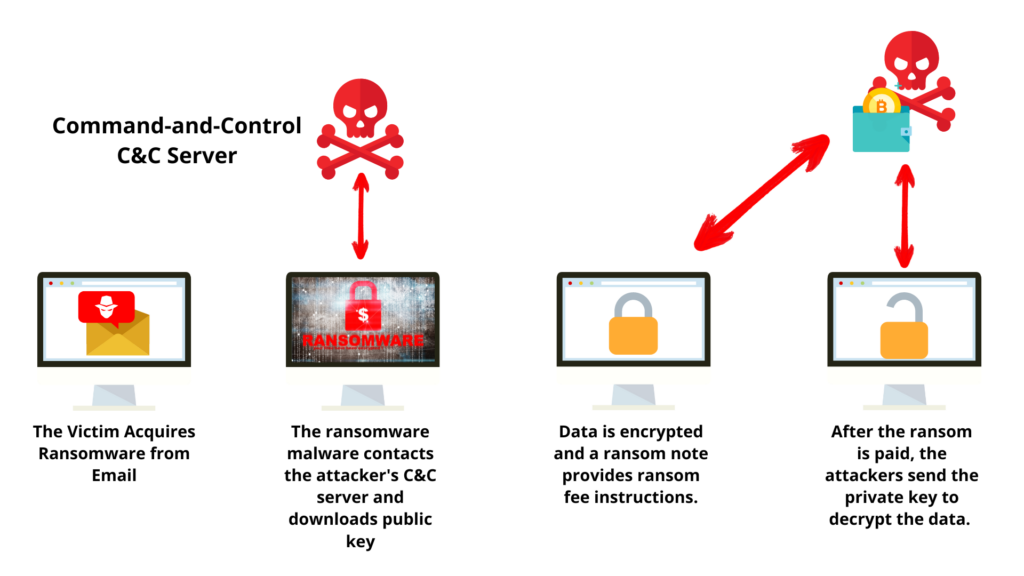 Professional visualization of ransomware attack on IT distribution infrastructure
Professional visualization of ransomware attack on IT distribution infrastructure
Timeline: July 3-7, 2025 - Multi-day outage affecting global operations
Attack Vector: Suspected infiltration through GlobalProtect VPN infrastructure
Threat Actor: SafePay ransomware group
Analysis: The Ingram Micro ransomware attack demonstrates the cascading impact of supply chain compromises on global IT infrastructure. As one of the world's largest IT distributors, the attack disrupted order processing and shipments for numerous enterprise customers, highlighting critical vulnerabilities in cloud-centric supply chain dependencies. The incident underscores the need for enhanced third-party risk management and supply chain resilience planning.
CISA Releases Thirteen Industrial Control Systems Advisories
Source: CISA Alerts & Advisories
Timeline: July 10, 2025 - Comprehensive ICS advisory release
Attack Vector: Multiple vulnerabilities across industrial control systems
Threat Actor: Various threat actors targeting critical infrastructure
CVE References:
- ICSA-25-191-01: Siemens SINEC NMS vulnerabilities
- ICSA-25-191-02: Siemens Solid Edge security flaws
- ICSA-25-191-03: Siemens TIA Administrator vulnerabilities
- ICSA-25-191-04: Siemens SIMATIC CN 4100 security issues
- ICSA-25-191-05: Siemens TIA Project-Server and TIA Portal flaws
Analysis: The simultaneous release of 13 ICS advisories indicates heightened threat activity against critical infrastructure. Siemens products feature prominently, suggesting coordinated vulnerability research or exploitation attempts. Organizations operating industrial control systems must prioritize these updates to prevent potential disruption to critical operations.
UK Arrests in 'Scattered Spider' Ransom Group
Source: Krebs on Security
Timeline: July 10, 2025 - Four arrests of individuals aged 17-20
Attack Vector: Social engineering and SIM-swapping operations
Threat Actor: Scattered Spider cybercrime group members
Analysis: The arrests of key Scattered Spider members, including Owen David Flowers and Thalha Jubair, represent significant law enforcement action against a prolific cybercrime group. The group's shift to targeting retail and airline sectors, combined with their sophisticated social engineering tactics, demonstrates the evolving threat landscape. Organizations must enhance employee security awareness training and implement robust identity verification procedures.
Multiple Critical Vulnerabilities Added to NIST NVD
Source: National Vulnerability Database
Timeline: July 13, 2025 - Multiple CVE publications and updates
Attack Vector: Various exploitation methods across different platforms
Threat Actor: Multiple threat actors exploiting known vulnerabilities
CVE References:
- CVE-2025-6554: Google Chrome V8 Type Confusion (CVSS 8.1) - Added to CISA KEV
- CVE-2025-24813: Apache Tomcat Path Equivalence (CVSS 9.8) - RCE vulnerability
- CVE-2025-24085: Apple Multiple Products Use-After-Free (CVSS 7.8) - Actively exploited
- CVE-2025-24993: Microsoft Windows NTFS Buffer Overflow (CVSS 7.8) - Local code execution
Analysis: The concentration of high-severity vulnerabilities across major platforms (Chrome, Tomcat, Apple, Windows) indicates a coordinated disclosure period or increased vulnerability research activity. The inclusion of multiple CVEs in CISA's KEV catalog confirms active exploitation, requiring immediate organizational response.
Strategic Threat Intelligence Analysis
Current threat intelligence indicates a convergence of advanced persistent threat (APT) activities with commodity malware distribution networks. The observed attack patterns demonstrate sophisticated reconnaissance capabilities combined with opportunistic exploitation of zero-day vulnerabilities. Key trends include:
Supply Chain Targeting: The Ingram Micro attack exemplifies threat actors' focus on high-impact supply chain nodes to maximize disruption across multiple organizations simultaneously.
Critical Infrastructure Focus: The release of 13 ICS advisories suggests coordinated reconnaissance or exploitation attempts against industrial control systems, potentially indicating nation-state involvement.
Authentication Bypass Techniques: Multiple vulnerabilities (Citrix NetScaler, Microsoft SPNEGO) target authentication mechanisms, suggesting threat actors are prioritizing initial access through credential bypass rather than traditional phishing.
Memory Corruption Exploitation: The prevalence of buffer overflow and use-after-free vulnerabilities indicates continued threat actor investment in memory corruption exploitation techniques.
Organizations should enhance monitoring for lateral movement indicators and implement advanced behavioral analytics to detect novel attack methodologies.
CISO Strategic Recommendations
Emergency Patch Management: Implement immediate patching for CVE-2025-5777 (Citrix NetScaler) and CVE-2025-47981 (Microsoft SPNEGO) within 24-48 hours. Establish war room protocols for critical vulnerability response.
Supply Chain Risk Assessment: Conduct comprehensive third-party risk assessments focusing on IT distributors and managed service providers. Implement continuous monitoring of vendor security postures.
Enhanced Authentication Controls: Deploy multi-factor authentication across all external-facing services, particularly VPN and remote access solutions. Implement session monitoring and anomaly detection.
Industrial Control Systems Security: For organizations with ICS environments, prioritize Siemens product updates and implement network segmentation between IT and OT environments.
Threat Hunting Activation: Initiate proactive threat hunting for Scattered Spider TTPs, focusing on social engineering attempts and SIM-swapping indicators.
Executive Communication: Prepare board-level briefings on supply chain risks and critical infrastructure vulnerabilities, emphasizing business continuity implications.
Incident Response Readiness: Test incident response procedures for supply chain disruption scenarios and ensure alternative vendor relationships are established.
Threat Landscape Analysis
The current threat landscape demonstrates increased sophistication in multi-vector attack campaigns targeting critical infrastructure and enterprise environments. Key observations include:
Threat Actor Evolution: Groups like Scattered Spider are demonstrating increased operational security and targeting precision, moving beyond opportunistic attacks to strategic sector targeting.
Vulnerability Weaponization Speed: The rapid exploitation of Citrix NetScaler vulnerabilities indicates threat actors have developed efficient vulnerability research and weaponization capabilities.
Critical Infrastructure Targeting: The focus on ICS vulnerabilities suggests potential preparation for disruptive attacks against critical infrastructure, possibly indicating geopolitical tensions.
Supply Chain Exploitation: The Ingram Micro attack demonstrates threat actors' understanding of supply chain dependencies and their potential for cascading impact.
Organizations must adopt zero-trust architecture principles and implement continuous security validation to maintain defensive effectiveness against evolving threat methodologies.
Conclusion and Forward-Looking Insights
The cybersecurity incidents analyzed around July 13, 2025, demonstrate the critical importance of proactive threat intelligence integration with operational security controls. The convergence of supply chain attacks, critical infrastructure targeting, and authentication bypass techniques indicates a maturing threat landscape requiring adaptive defensive strategies.
Key forward-looking considerations include:
Accelerated Patch Cycles: Organizations must develop capabilities for rapid vulnerability assessment and deployment, particularly for internet-facing systems.
Supply Chain Resilience: The Ingram Micro incident highlights the need for diversified vendor relationships and supply chain continuity planning.
Authentication Architecture: The prevalence of authentication bypass vulnerabilities necessitates zero-trust implementation and continuous authentication validation.
Critical Infrastructure Protection: The ICS advisory volume suggests increased focus on operational technology security and IT/OT convergence risks.
Future threat evolution will likely focus on AI-enhanced attack methodologies and supply chain exploitation, requiring adaptive defensive strategies and enhanced public-private threat intelligence sharing.
Sources and References
- Krebs on Security
- TheHackerNews
- CSO Magazine
- CISA Alerts & Advisories
- SecurityWeek
- National Vulnerability Database
- Infosecurity Magazine
- Cybersecurity Insiders
For more breach intelligence reports and cybersecurity insights, visit CISOPlatform.com and sign up to be a member.
Nominate for Global CISO 100 Awards & Future CISO Awards (1-2 October Atlanta, USA): Nominate Your Peer

Comments