CISOPlatform Breach Intelligence July 20, 2025 – Microsoft SharePoint Zero-Day, CoinDCX Crypto Exchange Hack, McDonald's AI Platform Breach
Executive Summary
The cybersecurity threat landscape on July 19, 2025 revealed 3 significant security incidents across critical infrastructure and enterprise environments. Key developments include a critical Microsoft SharePoint zero-day vulnerability (CVE-2025-53770) under active exploitation affecting 85+ organizations globally, a $44.2 million cryptocurrency exchange breach at CoinDCX, and a data exposure incident in McDonald's AI hiring platform. These incidents demonstrate sophisticated attack vectors targeting enterprise infrastructure, financial platforms, and AI-powered systems, requiring immediate defensive measures and strategic security posture alignment.
Key Breach Incidents Overview
- Critical Microsoft SharePoint Zero-Day Actively Exploited (CVE-2025-53770) - TheHackerNews
- CoinDCX Cryptocurrency Exchange Security Breach - $44.2M Loss - Multiple Sources
- McDonald's AI Hiring Platform Data Exposure - Fox News CyberGuy
- China-Sponsored U.S. National Guard Network Infiltration - Boston Institute of Analytics
- DotHouse Health ALPHV/BlackCat Ransomware Breach - HendryAdrian.com
Major Incident Analysis
Critical Microsoft SharePoint Zero-Day Actively Exploited (CVE-2025-53770)
Source: TheHackerNews

Timeline:
- July 18, 2025 ~18:00 UTC: First mass exploitation wave detected by Eye Security
- July 19, 2025 ~07:30 UTC: Second exploitation surge observed from new source IPs
- July 19, 2025: Microsoft publicly acknowledged active exploitation
- July 20, 2025: CISA issued emergency alert
Attack Vector: Unauthenticated remote code execution via deserialization of untrusted data in on-premises SharePoint Server. Attackers exploit CVE-2025-49706 (HTTP Referer manipulation) chained with CVE-2025-49704 (code injection) to achieve arbitrary command execution through the "ToolShell" exploit chain.
Threat Actor: Unknown sophisticated threat actors conducting mass exploitation campaign
Indicators of Compromise (IOCs):
spinstall0.aspx- Malicious ASPX web shell in TEMPLATE\LAYOUTS directory107.191.58.76- Exploit source IP104.238.159.149- Exploit source IP96.9.125.147- Exploit source IP- POST requests to
/_layouts/15/ToolPane.aspx?DisplayMode=Edit&a=/ToolPane.aspx - Referer header:
/_layouts/SignOut.aspx
CVE References:
- CVE-2025-53770 (CVSS 9.8): Deserialization vulnerability enabling unauthenticated RCE
- CVE-2025-49706 (CVSS 6.3): SharePoint spoofing/authentication bypass via HTTP Referer manipulation
- CVE-2025-49704 (CVSS 8.8): SharePoint code injection vulnerability
MITRE ATT&CK Mapping:
- T1190 (Initial Access): Exploit Public-Facing Application
- T1505.003 (Persistence): Web Shell
- T1078 (Defense Evasion): Valid Accounts (via stolen MachineKey)
- T1027 (Defense Evasion): Obfuscated Files or Information (Base64 PowerShell)
- T1083 (Discovery): File and Directory Discovery
Analysis: This represents one of the most significant zero-day exploitation campaigns of 2025. The sophisticated "ToolShell" attack chain demonstrates advanced threat actor capabilities, combining multiple vulnerabilities to achieve persistent access. The theft of SharePoint MachineKey cryptographic material enables attackers to forge valid authentication tokens, making detection and remediation extremely challenging. With 85+ confirmed compromised servers across 29 organizations including government entities, this incident highlights critical gaps in enterprise patch management and network segmentation strategies.
CoinDCX Cryptocurrency Exchange Security Breach
Source: Multiple Cybersecurity Sources

Timeline:
- July 19, 2025 (early hours IST): Unauthorized access detected to internal operational wallet
- July 19, 2025: Blockchain analyst ZachXBT flags suspicious transactions
- July 19, 2025: CoinDCX publicly discloses breach after 17-hour investigation
Attack Vector: Sophisticated server breach targeting internal operational account used for liquidity provisioning with partner exchange. Attackers gained access to untagged hot wallet not included in proof-of-reserves disclosures.
Threat Actor: Unknown sophisticated cybercriminals with advanced cryptocurrency laundering capabilities
Indicators of Compromise (IOCs):
- Funds laundered through Tornado Cash mixer
- Cross-chain bridging from Solana to Ethereum networks
- Approximately $44.2 million USD (₹378 crore) stolen from operational wallet
Analysis: This incident represents a significant evolution in cryptocurrency exchange attack methodologies, targeting operational infrastructure rather than customer-facing systems. The attackers demonstrated sophisticated understanding of exchange architecture by specifically targeting liquidity provisioning wallets that fall outside standard security monitoring. The 17-hour delay in public disclosure, while the exchange conducted internal investigation, highlights the challenge of balancing thorough incident response with transparency requirements. CoinDCX's commitment to absorb the loss from treasury reserves demonstrates mature incident response planning, though the incident underscores persistent vulnerabilities in centralized exchange security models.
McDonald's AI Hiring Platform Data Exposure
Source: Fox News CyberGuy
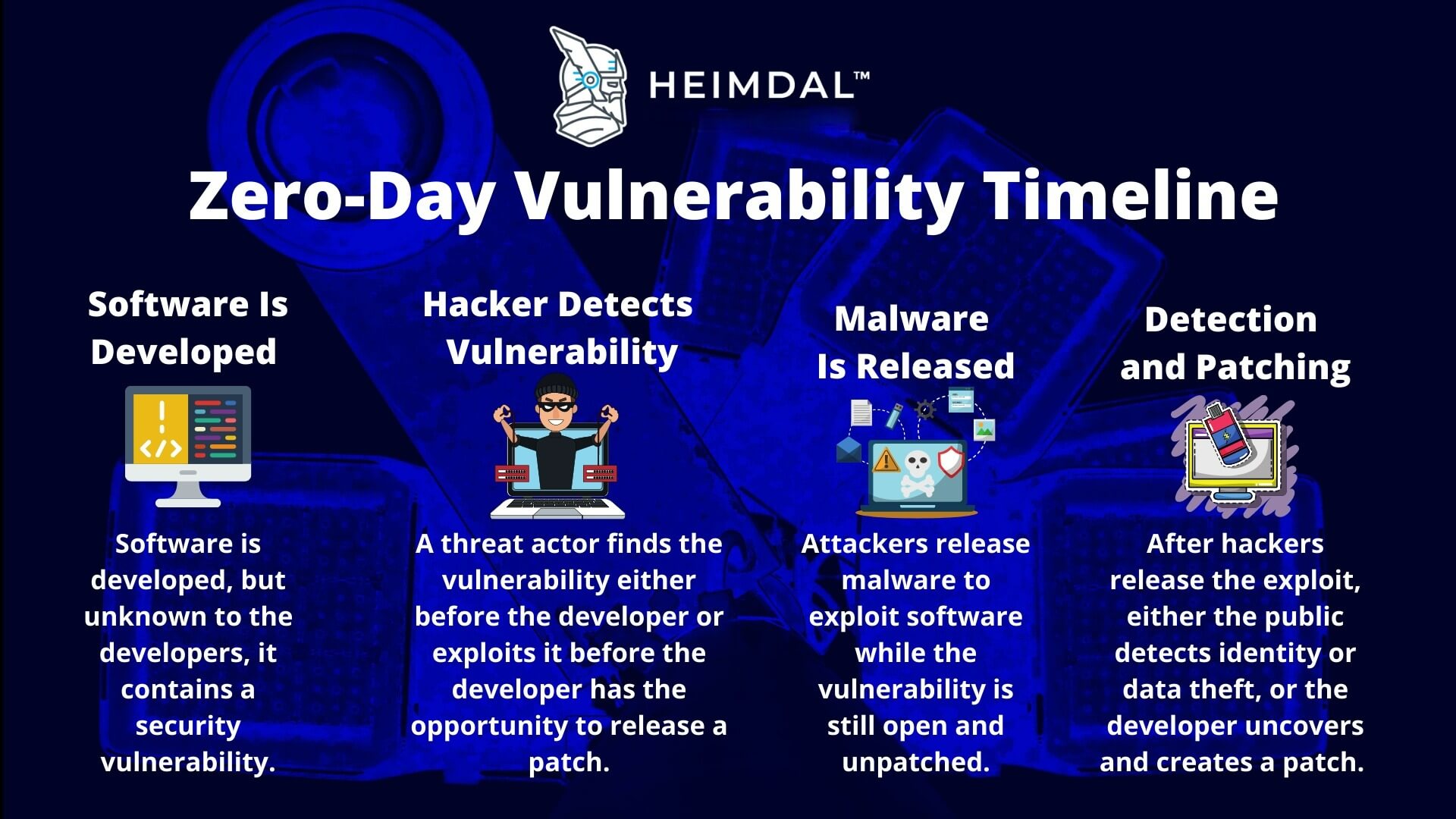
Timeline:
- June 30, 2025: Security researchers Ian Carroll and Sam Curry discovered vulnerability
- July 19, 2025: Public disclosure of incident affecting 5 job candidates
Attack Vector: Exploitation of outdated credentials in Paradox.ai test account used by McDonald's McHire platform, accessing unauthenticated API endpoint.
Threat Actor: Security researchers conducting responsible disclosure (Ian Carroll and Sam Curry)
Analysis: While limited in scope affecting only 5 individuals, this incident highlights critical security gaps in AI-powered enterprise systems. The exposure of a forgotten test account with production data access demonstrates insufficient decommissioning procedures for development environments. The rapid vendor response and remediation within hours of notification represents industry best practices for responsible disclosure handling. However, the incident underscores the need for comprehensive security auditing of third-party AI platforms and strict credential lifecycle management in AI-driven business processes.
Strategic Threat Intelligence Analysis
Current threat intelligence indicates a significant escalation in zero-day exploitation campaigns targeting enterprise infrastructure, with particular focus on collaboration platforms and financial systems. The Microsoft SharePoint campaign demonstrates sophisticated threat actor capabilities combining multiple vulnerabilities in coordinated attack chains. Cryptocurrency platforms continue to face targeted attacks exploiting operational infrastructure vulnerabilities rather than customer-facing systems. The emergence of AI platform security incidents signals a new attack surface requiring specialized security controls. Organizations should enhance monitoring for lateral movement indicators, implement advanced behavioral analytics for anomalous network traffic, and prioritize zero-trust architecture implementation for critical business systems.
CISO Strategic Recommendations
- Emergency Patch Management: Implement immediate SharePoint server isolation and AMSI integration pending Microsoft patch release
- Enhanced Cryptocurrency Controls: Deploy comprehensive monitoring for operational wallet activities and implement multi-signature requirements
- AI Platform Security Auditing: Conduct thorough security assessments of all third-party AI systems with data access capabilities
- Zero-Day Response Protocols: Activate enhanced threat hunting for similar attack vector identification across enterprise infrastructure
- Executive Briefing: Schedule board-level security posture review focusing on supply chain and third-party risk management
Threat Landscape Analysis
The current threat landscape demonstrates unprecedented sophistication in multi-vector attack campaigns targeting critical business infrastructure. Threat actors are leveraging advanced reconnaissance techniques to identify and exploit operational systems that fall outside traditional security monitoring scope. The convergence of zero-day exploitation, cryptocurrency targeting, and AI platform vulnerabilities indicates threat actors are adapting to modern enterprise technology stacks. Organizations must adopt comprehensive security architectures that address both traditional infrastructure and emerging technology platforms. The observed attack patterns suggest increased focus on persistence mechanisms that blend with legitimate business operations, requiring advanced behavioral analytics and continuous security validation.
Conclusion and Forward-Looking Insights
The cybersecurity incidents of July 19, 2025 demonstrate the critical importance of proactive threat intelligence integration with operational security controls. The Microsoft SharePoint zero-day campaign represents a watershed moment in enterprise security, highlighting the devastating impact of coordinated vulnerability exploitation. Cryptocurrency platform security continues to evolve, with attackers targeting operational infrastructure rather than customer assets. The emergence of AI platform security incidents signals the need for specialized security frameworks addressing artificial intelligence systems. Organizations must prioritize continuous monitoring, rapid response capabilities, and strategic threat intelligence consumption to maintain effective security posture against increasingly sophisticated threat actors.

Comments