CISOPlatform Breach Intelligence July 22, 2025 – Microsoft SharePoint Zero-Day Exploits, Mass Cryptojacking Campaign, Chrome ANGLE Vulnerability
Executive Summary
The cybersecurity threat landscape on July 21, 2025 revealed critical security incidents with immediate enterprise impact. The most significant development was the active exploitation of Microsoft SharePoint Server zero-day vulnerabilities (CVE-2025-53770, CVE-2025-53771) affecting 75+ organizations globally, including federal agencies, universities, and energy companies. Additional threats included a mass cryptojacking campaign compromising 3,500+ websites and critical vulnerabilities in Chrome ANGLE/GPU sandbox and NVIDIA Container Toolkit. Organizations must prioritize immediate SharePoint patching, ASP.NET machine key rotation, and enhanced monitoring for lateral movement indicators while maintaining strategic security posture alignment with current threat intelligence.
Key Breach Incidents Overview
- Critical Microsoft SharePoint Zero-Day Actively Exploited, Breaches 75+ Company Servers - TheHackerNews
- Microsoft Releases Urgent Patch for SharePoint RCE Flaw Exploited in Ongoing Cyber Attacks - TheHackerNews
- Microsoft Rushes Emergency Patch for Actively Exploited SharePoint 'ToolShell' Bug - Dark Reading
- Microsoft SharePoint zero-day breach hits on-prem servers - CSO Magazine
- Microsoft Fix Targets Attacks on SharePoint Zero-Day - Krebs on Security
- Microsoft: Attackers Actively Compromising On-Prem SharePoint Customers - Infosecurity Magazine
- Mass Cryptojacking Campaign Hits Over 3,500 Websites - TheHackerNews
- Chrome ANGLE/GPU Sandbox Escape Vulnerability Actively Exploited - TheHackerNews
Major Incident Analysis
Microsoft SharePoint Zero-Day Exploitation Campaign (CVE-2025-53770, CVE-2025-53771)
Source: TheHackerNews, Dark Reading, CSO Magazine, Krebs on Security

• July 18, 2025 (6:00 PM CET): Active exploitation begins
• July 20, 2025: CISA adds CVE-2025-53770 to Known Exploited Vulnerabilities catalog
• July 21, 2025: Microsoft releases emergency patches for both vulnerabilities
/_layouts/15/ToolPane.aspx with spoofed Referer headers.Indicators of Compromise (IOCs):
spinstall0.aspx- Malicious ASPX payload file- POST requests to
/_layouts/15/ToolPane.aspx - Spoofed Referer header:
_layouts/SignOut.aspx - PowerShell execution for MachineKey extraction
- Anomalous SharePoint service restarts
• CVE-2025-53770 (CVSS 9.8): Remote code execution via deserialization of untrusted data in SharePoint Server
• CVE-2025-53771 (CVSS 7.1): Spoofing vulnerability enabling path traversal in SharePoint
• CVE-2025-49706 (CVSS 6.3): Authentication bypass vulnerability (chained)
• CVE-2025-49704 (CVSS 8.8): Code injection vulnerability (chained)
• T1190 (Initial Access): Exploit Public-Facing Application
• T1059.001 (Execution): PowerShell execution for credential harvesting
• T1505.003 (Persistence): Web Shell deployment via ToolShell backdoor
• T1552.004 (Credential Access): Private Keys extraction (ASP.NET MachineKey)
• T1021.001 (Lateral Movement): Remote Services via compromised SharePoint integration
Analysis: This represents a critical supply chain attack targeting enterprise collaboration infrastructure. The sophistication of vulnerability chaining demonstrates advanced threat actor capabilities with deep understanding of SharePoint architecture. The theft of ASP.NET machine keys enables persistent access and lateral movement across integrated Microsoft services (Teams, OneDrive, Outlook). Organizations with internet-facing SharePoint servers should assume compromise and implement immediate containment measures.
Mass Cryptojacking Campaign Targeting 3,500+ Websites
Source: TheHackerNews
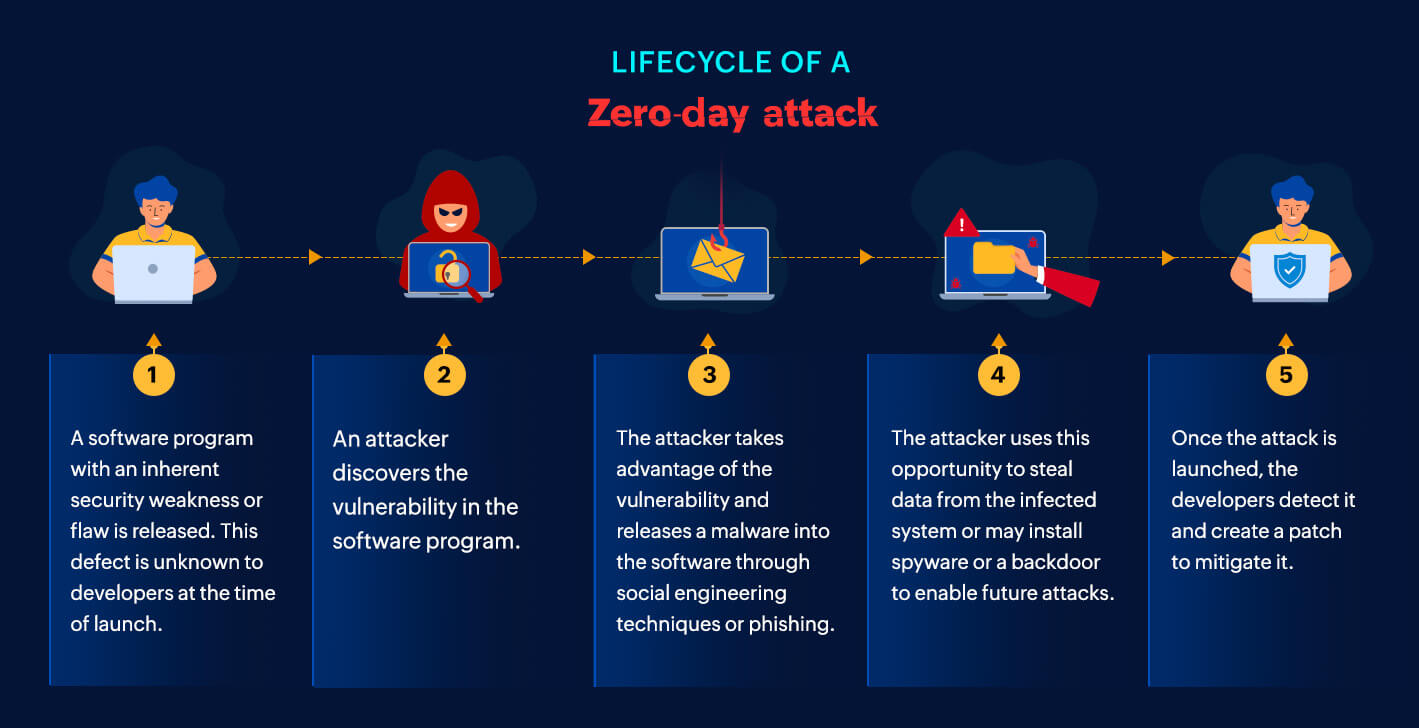
• July 21, 2025: Security researchers discover widespread JavaScript-based cryptomining campaign
• Ongoing: Dynamic payload delivery via WebSocket connections
Indicators of Compromise (IOCs):
- Obfuscated JavaScript miners in website source code
- WebSocket connections to cryptomining pools
- Background Web Worker processes consuming CPU cycles
- Dynamic thread adjustment based on system monitoring
Analysis: This campaign demonstrates evolution in cryptojacking methodologies with advanced evasion capabilities. The use of WebSocket protocols for dynamic payload delivery and resource-aware mining optimization indicates sophisticated threat actor capabilities. Organizations should implement enhanced web application security monitoring and client-side protection mechanisms.
Strategic Threat Intelligence Analysis
Current threat intelligence indicates a convergence of advanced persistent threat (APT) activities with sophisticated vulnerability exploitation targeting enterprise collaboration platforms. The SharePoint zero-day campaign demonstrates threat actor evolution toward supply chain attacks against critical business infrastructure. The simultaneous emergence of advanced cryptojacking campaigns and browser sandbox escape vulnerabilities suggests coordinated threat actor activities across multiple attack vectors. Organizations must enhance monitoring for lateral movement indicators, implement advanced behavioral analytics for anomalous network traffic detection, and prioritize zero-trust architecture implementation to counter evolving threat methodologies.
CISO Strategic Recommendations
- Immediate SharePoint Remediation: Apply CVE-2025-53770/53771 patches within 24 hours, rotate ASP.NET machine keys, restart IIS services, and enable AMSI integration across all SharePoint farms
- Enhanced Threat Hunting: Deploy advanced behavioral analytics for SharePoint anomalous access patterns, PowerShell execution monitoring, and lateral movement detection across Microsoft 365 integration points
- Zero-Trust Implementation: Accelerate migration to SharePoint Online with centralized security controls, implement network segmentation for on-premises SharePoint servers, and deploy multi-factor authentication for all administrative access
- Supply Chain Security Assessment: Conduct comprehensive third-party risk assessment for collaboration platform dependencies, implement continuous security validation for web applications, and establish incident response protocols for supply chain compromises
- Executive Security Briefing: Schedule board-level security posture review focusing on collaboration platform security, threat landscape evolution, and strategic security investment priorities
Threat Landscape Analysis
The current threat landscape demonstrates unprecedented sophistication in multi-vector attack campaigns targeting critical enterprise infrastructure. Threat actors are leveraging zero-day vulnerabilities in collaboration platforms to achieve persistent access across integrated business systems. The emergence of advanced cryptojacking campaigns with evasion capabilities indicates threat actor adaptation to enhanced security controls. Browser sandbox escape vulnerabilities and container runtime exploits suggest systematic targeting of modern application architectures. Organizations must adopt comprehensive security strategies encompassing zero-trust principles, continuous monitoring, and rapid response capabilities to maintain defensive effectiveness against evolving threat methodologies targeting business-critical infrastructure.
Conclusion and Forward-Looking Insights
The cybersecurity incidents analyzed on July 21, 2025 demonstrate the critical importance of proactive vulnerability management and integrated security architecture for enterprise collaboration platforms. The SharePoint zero-day exploitation campaign highlights the risks of internet-facing collaboration infrastructure and the need for accelerated cloud migration strategies. Future threat evolution will likely focus on supply chain attacks against business-critical platforms, advanced evasion techniques for cryptojacking campaigns, and systematic exploitation of container and browser security boundaries. Organizations must prioritize continuous security validation, rapid patch deployment capabilities, and strategic threat intelligence integration to maintain effective security posture against sophisticated threat actors targeting enterprise infrastructure.
Sources and References
- TheHackerNews - Critical Microsoft SharePoint Zero-Day
- TheHackerNews - Microsoft SharePoint Patch Release
- Dark Reading - SharePoint ToolShell Bug
- CSO Magazine - SharePoint Zero-Day Analysis
- Krebs on Security - SharePoint Attack Analysis
- Infosecurity Magazine - SharePoint Compromise Report
- CISA Known Exploited Vulnerabilities Catalog
- Eye Security - ToolShell Analysis
- Palo Alto Networks Unit 42 - Threat Intelligence
For more breach intelligence reports and cybersecurity insights, visit CISOPlatform.com and sign up to be a member.
Nominate for Global CISO 100 Awards & Future CISO Awards (1-2 October Atlanta, USA): Nominate Your Peer

Comments