We had “Best Of The World In Security” Webinar On "DevOps Lesson For Your SOC (SRE)". We discussed Google-inspired lessons of transforming detection and response practices using the approach we call Autonomic Security Operations. DevOps transformed IT and changed roles, practices and skills within IT. Security in general and security ops, in particular, are sometimes left behind.
Session Agenda
- How does the security analyst role evolve?
- How security processes change in an ASO SOC?
- How automation reduces toil (and what is toil, anyway)
About Speaker
Dr. Anton Chuvakin, Past Gartner Analyst and very well known in the information security community. He is currently the security advisor at Office Of The CISO At Google Cloud. He is a recognized security expert in the field of SIEM, log management and PCI DSS compliance.
(Webinar) Recorded
Discussion Highlights
1. 2003 or 2023? Sec Ops is Ripe for Transformation
- We can’t store and analyze all data, resulting in blindspots
- It’s cost prohibitive to ingest all the data we need
- It takes too long to investigate alerts
- We struggle to build effective detection and have too many false positives/negatives
- Our processes are too manual, we are too slow to respond to and remediate threats
- We don’t have enough skilled engineers to make everything work
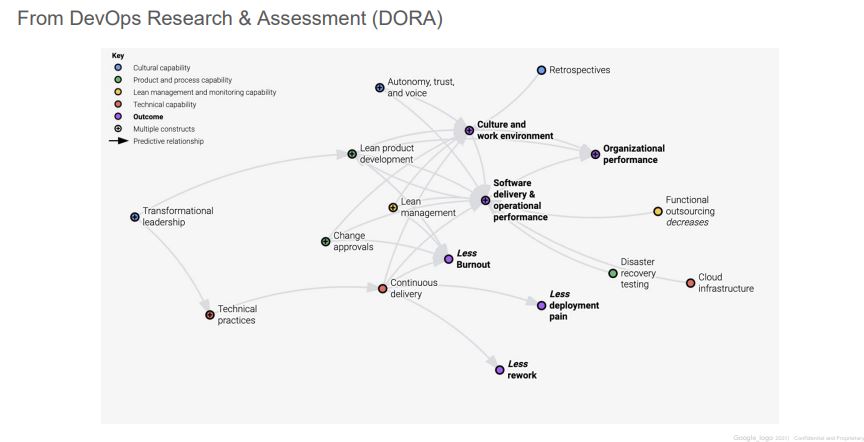
2. What Outcomes did DevOps / SRE achieve?
3. Google vs Enterprise “SecOps”
- What does Google do?
- Automation/SRE is a mindset – part of the hiring process, part of OKRs, and performance reviews
- Requires coding interviews, high pay, attracts the best, invests in growth
- 40/40/20 between eng, operations, and learning
- Investment in efficiency solves for human costs
- Intel strongly embedded in D&R, mostly utilized towards proactive work, strong collaboration across Alphabet & benefits from developer hygiene
- What do most enterprises do?
- Experimenting with SOAR, full adoption is tough due to minimal automation culture
- Hires traditional roles, no coding, rarely outsources, less pay, less growth, more stress
- Utilization is almost always >100%
- Cost-prohibitive data ingestion, oftentimes paying SIEM + DIY, increasing $ from complexity
- CTI team produces great reports, SOC consistently doing fire drills, >90% false positive rate, uneven distribution of skill (Tier 3)
4. Autonomic Security Operations Principles:
- ASO should
- Eliminate toil
- Embrace change
- Strive for continuous improvement
- Bridge all siloes
- Use service level objectives
- Avoid hero mentality
- Aim for simplicity
- ASO should not
- Restrict hiring to top professionals
- Require an engineering-only culture
- Increase overall tooling footprint
- Aim for incremental gain
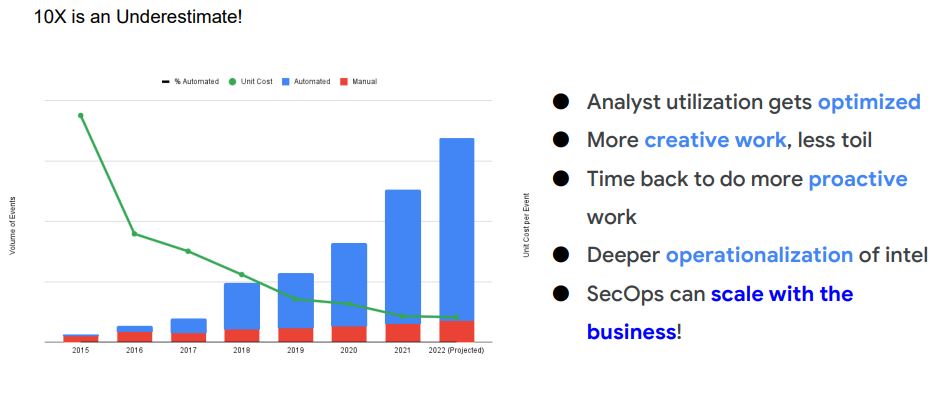
5. Eliminate Toil : manual, repetitive, automatable, tactical, devoid of enduring value, and that scales linearly as a service grows
- Causes of Toil
- Too much technical debt
- Priorities or goals are not aligned
- Lack of training or support
- Lack of collaboration
- The business value to fix is too hard to realize
- Less Gathering, More Analysis – basics to automate
- Gathering machine information
- Gathering user information
- Process executions
- All context needed to help get to final (human) judgement
- Key Activities To Implement
- Train your team on toil & automation
- Create an Automation Queue
- Implement Blameless Postmortems
- Conduct Weekly Incident Reviews
- Implement SOAR
- Hire Automation Engineer(s)
- Implement CD/CR pipelines with metrics
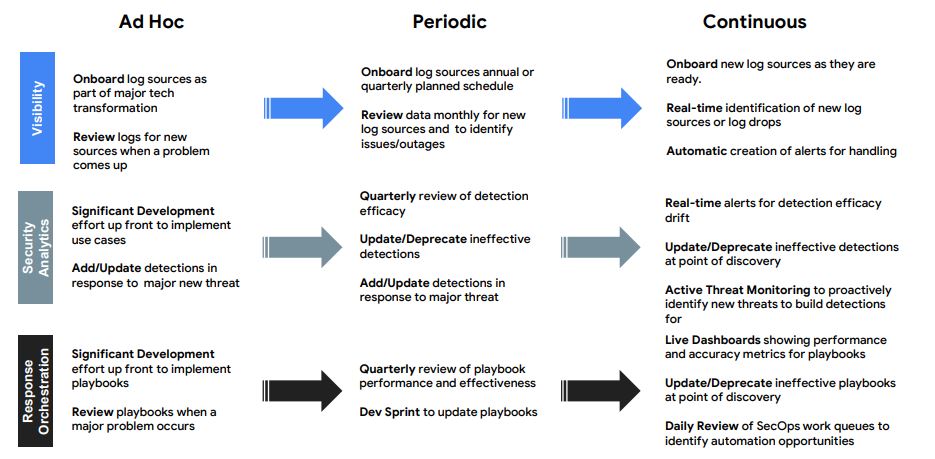
6. Evolve Automation
7. Practice Release Engineering
8. Strive for Simplicity
Complex systems require substantial human expertise in their operation and management. This expertise changes in character as technology changes but it also changes because of the need to replace experts who leave. In every case, training and refinement of skill and expertise is one part of the function of the system itself. At any moment, therefore, a given complex system will contain practitioners and trainees with varying degrees of expertise. Critical issues related to expertise arise from (1) the need to use scarce expertise as a resource for the most difficult or demanding production needs and (2) the need to develop expertise for future use.
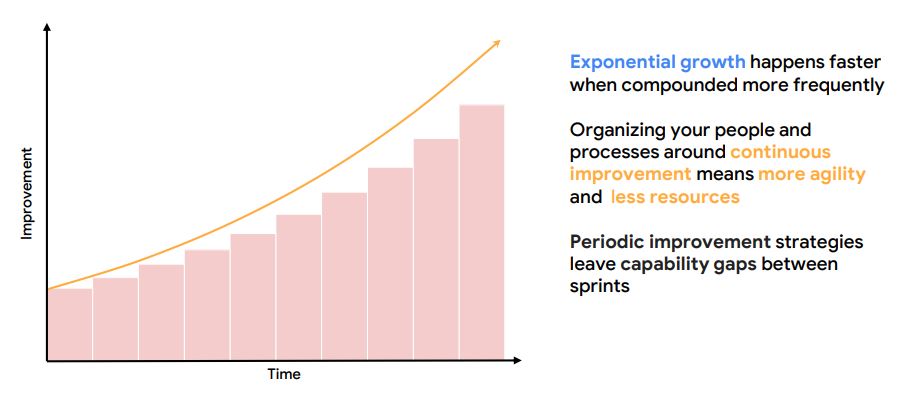
9. The Power of Continuous Improvement
10. Actions
- Reduce toil in your SOC - shift toil to machines
- Evolve automation in SIEM, SOAR, threat intel, etc
- Use SLOs / metrics to drive change
- Practice release engineering for consistent improvement
- Strive for simplicity with processes, technology stack, etc

Comments