We had a community webinar on "From Chaos To Control : Lessons Learned From The Ransomware Attack". We discussed the importance of cybersecurity and the growing threat of ransomware attacks. Described the specific incident we experienced, highlighting the impact on our organization and the challenges we faced. Key lessons we learned from the incident, including what worked well and what could have been done differently. Emphasize the importance of having a comprehensive backup and employee training.
Session Agenda
- Importance of having a comprehensive incident response plan
- Need for regular backups and employee training
- Best practices for preventing ransomware attacks
- Need for ongoing monitoring and testing of security measures to ensure they are effective and up to date
- Importance of learning from the experience and continually improving security measures to stay ahead of evolving threats
About Speaker
Prabhakar Ramakrishnan, CISO & General Manager - IT Infrastructure at TNQ Technologies
(PPT) Presentation From The Discussion
Discussion Highlights
1. Growing Threat of Ransomware Attacks
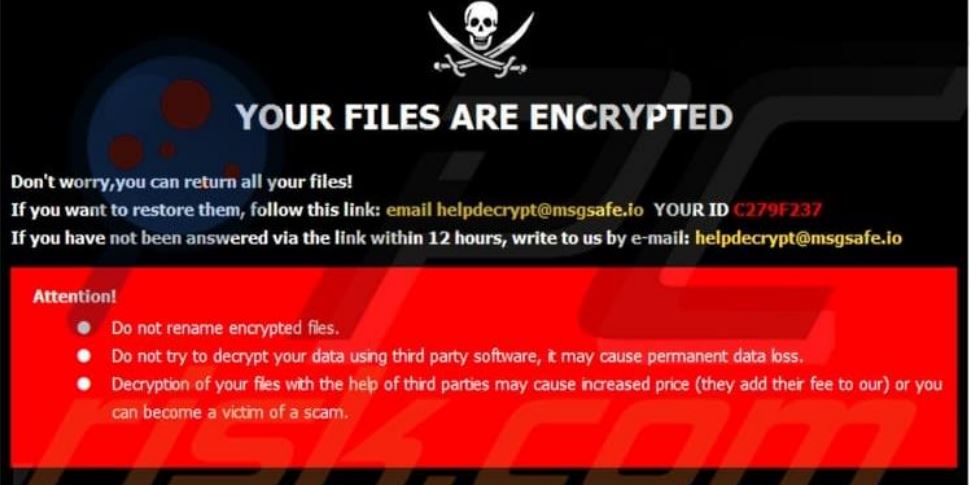
- Ransomware is a type of malware that encrypts files on a victim's computer system, making them inaccessible until a ransom is paid
- The threat of ransomware attacks is growing as cybercriminals are becoming more sophisticated and using new tactics such as double extortion, where they not only encrypt the victim's data but also threaten to leak it if the ransom is not paid
2. Impact of Ransomware Attacks
- Ransomware attacks can have a devastating impact on individuals and organizations, causing financial losses, reputational damage, and even legal liabilities
- In addition to the direct costs of paying the ransom and restoring the encrypted data, there are also indirect costs such as lost productivity, business interruption and regulatory compliance
3. Personal experience and lessons learned :
Backup - RPO : 2hours, 8hours, 24hours
Incident Response Plan
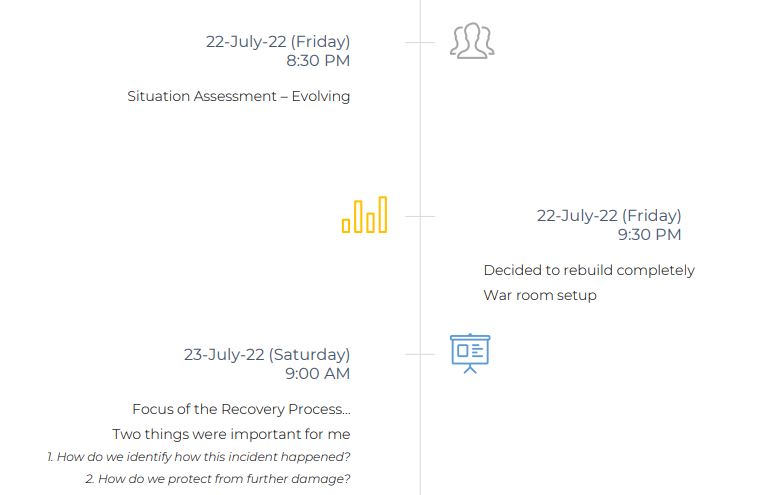
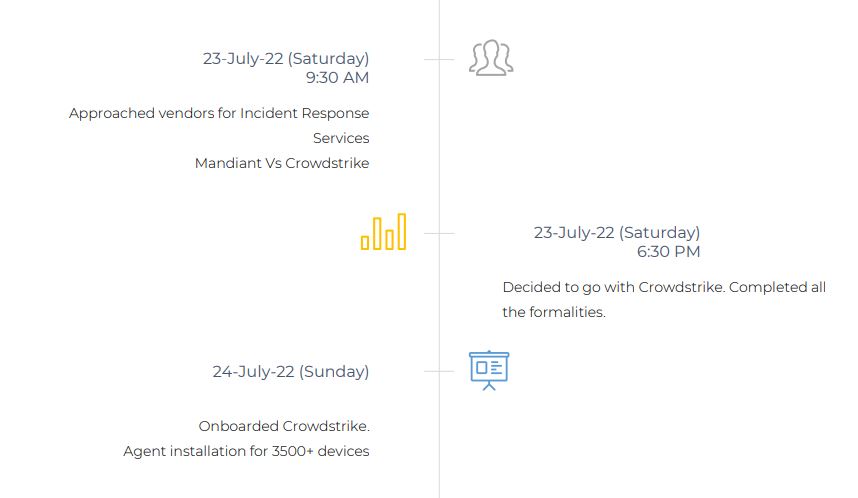
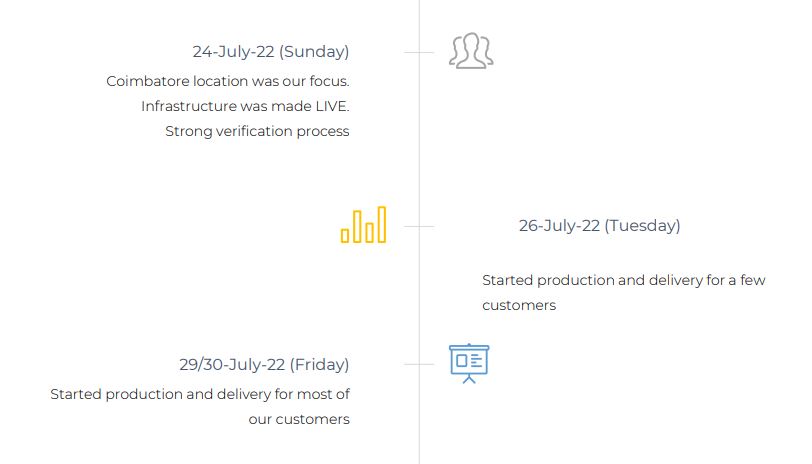
4. How we recovered
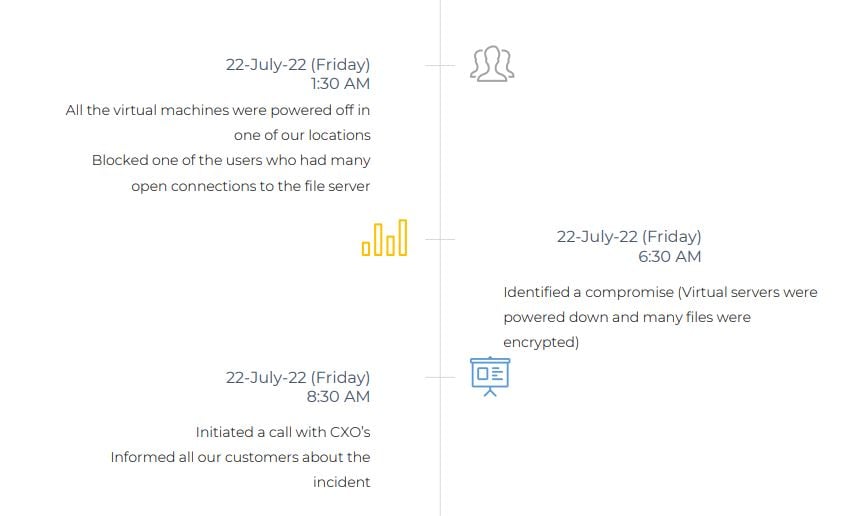
5. Incident Summary
- Threat actor used a compromised account to access the servers over RDP
- Using the Admin account the Threat actor copied and installed an open-source softwarefor anonymous communication named TOR (The Onion Router). During this installation, Threat Actor masqueraded the anonymity software TOR as Applocker.exe which is a legitimate Microsoft Windows application
- TOR is an open-source software that creates a multi-hop proxy network which allows Threat Actors to communicate with the installed systems over an encrypted channel
- To further maintain persistence in the environment, the Threat Actor installed multiple remote management software like Atera agent, AnyDesk, LogMeIn and BitVise and ZeroTier
- Threat Actor attempted to perform lateral movement by installing the Remote Management tool named Action1
- Threat Actor used the compromised privileged account to copy a compressed file which contained multiple legitimate system administration tools, different variants of ransomware encryptor and text files
- Threat Actor created an account MS_BACKUP on the Domain controller and added the Account Domain Admin Group
6. Ransomware Deployment Activity
- The Threat Actor copied multiple binaries of Windows and Linux based ALPHV ransomware encryptors to the system
- The Threat Actor targeted ESXi systems by copying the Linux ALPHV ransomware executable and linkable format (ELF) binaries on multiple VMware ESXi systems
- Once connected to the ESXi systems through SSH connections using the root account, the Threat Actor copied over the ALPHV ELF binary encryptor to the ESXi systems and executed the ransomware encryptor. This resulted in the encryption of several virtual machine disk (VMDK) files stored on the datastore attached to these ESXi systems
7. Major Gap’s
- EDR was not installed in the servers that were compromised
- Weak password, Same password used for multiple devices
- 2FA was not configured for all external facing applications
- Backups stored in the same environment
- Lack of centralized logging
8. Important Documents
- Situational Awareness Report
- Communication Plan
- Recovery Process

Comments