We had a community webinar on "Zero Trust : Architecture Principles; Threats; Architecture Components; Guidance Documents - NIST, CISA, NSA, DOD". We discussed history of the zero trust model, why is it relevant now ? (perimeter is dead, people work from anywhere and data is on endpoints and in the cloud), Zero trust architecture principles and tenets, Zero trust threats, Zero trust architecture components, Policy enforcement point types, Cloud deployment models, Zero trust guidance documents - NIST, CISA, NSA, DOD and more.
Session Agenda
- History of the zero trust mode
- Why is it relevant now ? (perimeter is dead, people work from anywhere and data is on endpoints and in the cloud)
- Zero trust architecture principles and tenets
- Zero trust threats
- Zero trust architecture components
- Policy enforcement point types
- Cloud deployment models
- Zero trust guidance documents - NIST, CISA, NSA, DOD
About Speaker
Wayne Tufek (Frequent Speaker RSAConference APJ, ISC 2, SACON & Renowned Security Architect) Wayne is currently on the board of the Melbourne Chapter of ISACA and holds the position of Vice President.
(Webinar) Recorded
Discussion Highlights
1. Why Zero Trust?
- Previous security models did not holistically apply important well known security principles
- Most Security architectures are like a cocunut
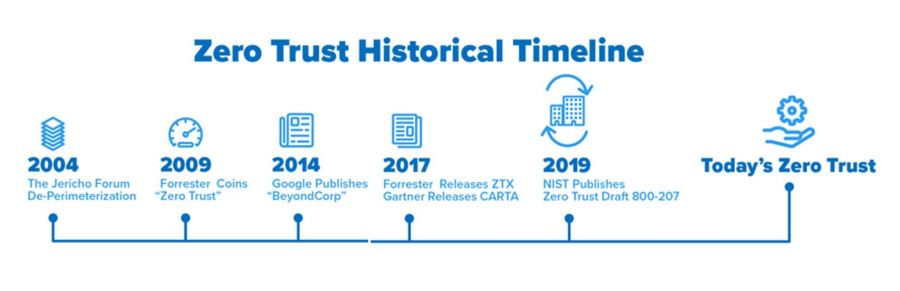
2. History of Zero Trust
3. Definition of Zero Trust
- Security model and set of design principles
- Threats exist both inside and outside traditional network boundaries
- Model Eliminates implicit trust in any one element
- Instead requires continuous verification
- Via real time information from multiple sources
- Model assumes that a breach is inevitable or has likely already occurred
- Limits access to what is needed and looks for anomalous or malicious activity
- Embeds comprehensive security monitoring; granular risk based access controls
- Data centric model allows the concept of least privilege to be applied for every access decision
4. Tenets
- Identity & Inventory is key - know your users, devices, services and data
- Trust is not based on device's network location - the network is always assumed to be hostile
- Every device, User and network flow is authenticated and authorised
- Access is based on context, for example the identity of the user, the device being used etc
- Devices may be company owned or owned by the User
- Access is granted on a per session basis
- All communication is secure
- Access to resources is determined by dynamic policy and observable state
- Strong authentication is used
- Continuous logging, monitoring and posture assessment
- Monitoring should be an ongoing basis to access risk, access is adaptive and varies based on context
- Assume breach - an attacker is already on our network
- External and Internal threats exist at all times
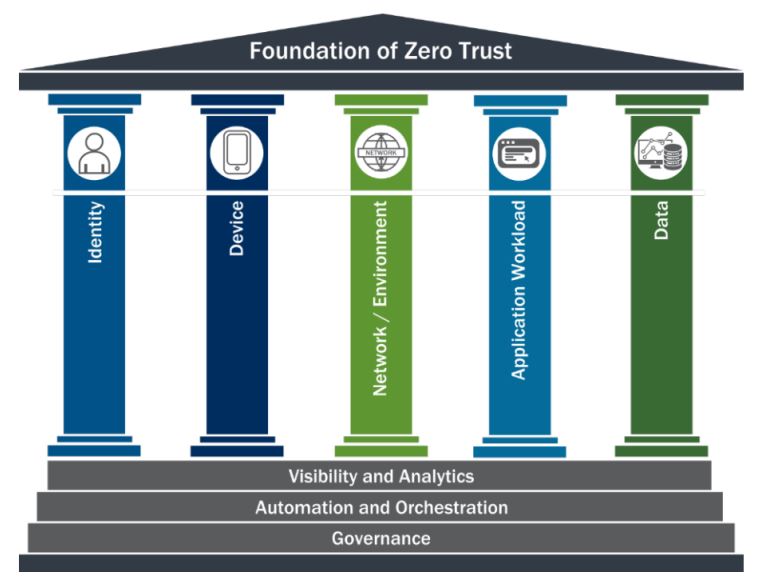
5. Foundation Of Zero Trust
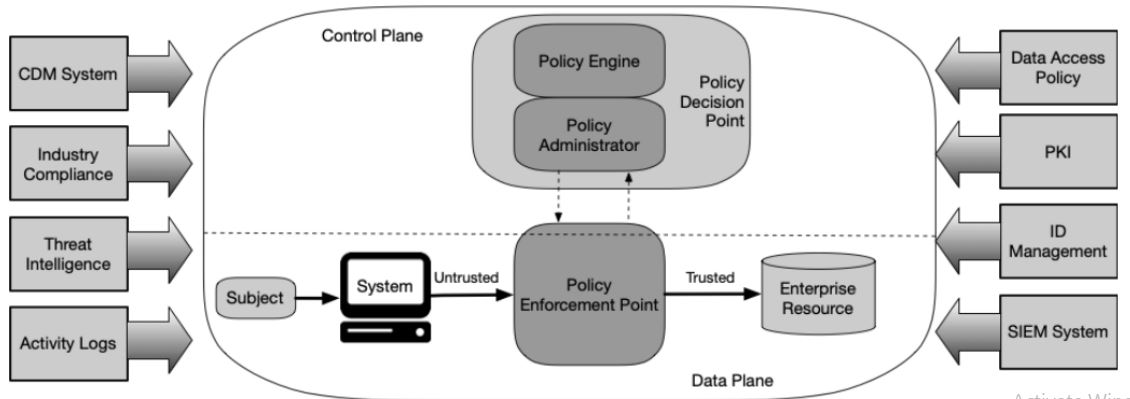
6. Logical Components
7. Benefits
- Support work from anywhere
- Prevention First
- Protect resources regardless of their location
- Better address threats
- Limit an attacker's ability to move laterally
- Users connect directly to services and not to the network
- Improve incident detection and response
- Improve visibility
- Dynamic risk-based assessments = better defence
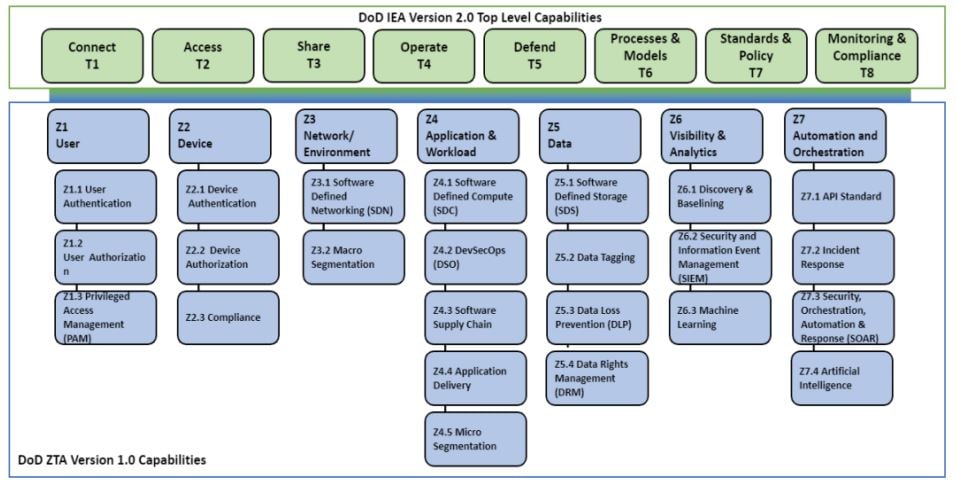
8. Capabilities and Services
9. Implementing Zero Trust
- Users
- Centralised enterprise managed identities
- MFA (application layer enforcement, Phishing resistant, passwords)
- Check password against known breaches
- At least one device level signal during authentication
- PAM
- ABAC
- RBAC
- Devices
- Maintain a complete reliable inventory of assets
- EDR
- Networks
- Network visibility
- Encrypt DNS requests
- Use HTTPS for web application and APIs
- Plan for Network isolation
- Applications and Workloads
- Understand your network protect surface
- Treat all applications as internet connected
- Have a dedicated application security testing program
- Operate an effective and welcoming public vulnerability disclosure program
- Work towards employing immutable workloads
- Data
- Categorise and tag your assests
- Audit access to any data encrypted at rest in a commercial cloud
- Implement comprehensive logging
- Automate security responses
- Key Steps
- Decide to adopt a zero trust strategy
- Inventory your environment
- Determine your current state
- Set desired maturity
- Don't forget governance
- Start with identity and device security
- Slow and steady - work with your existing capabilities first
- Ditch passwords
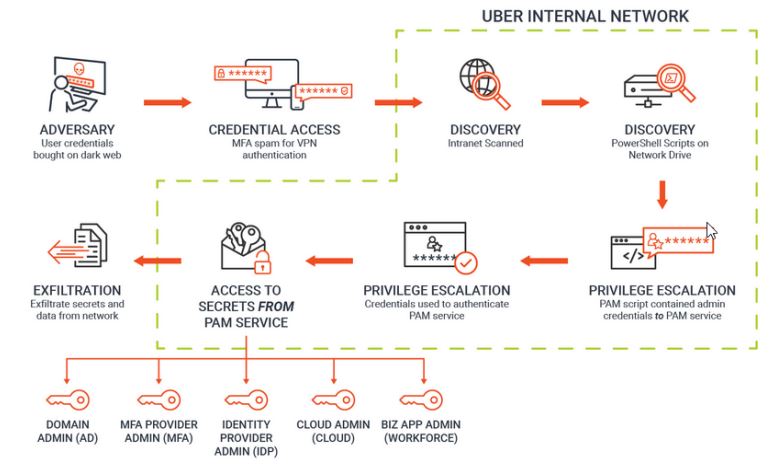
10. Zero Trust In Action : Deconstructing the Uber Attack - what we reportedly know

Comments