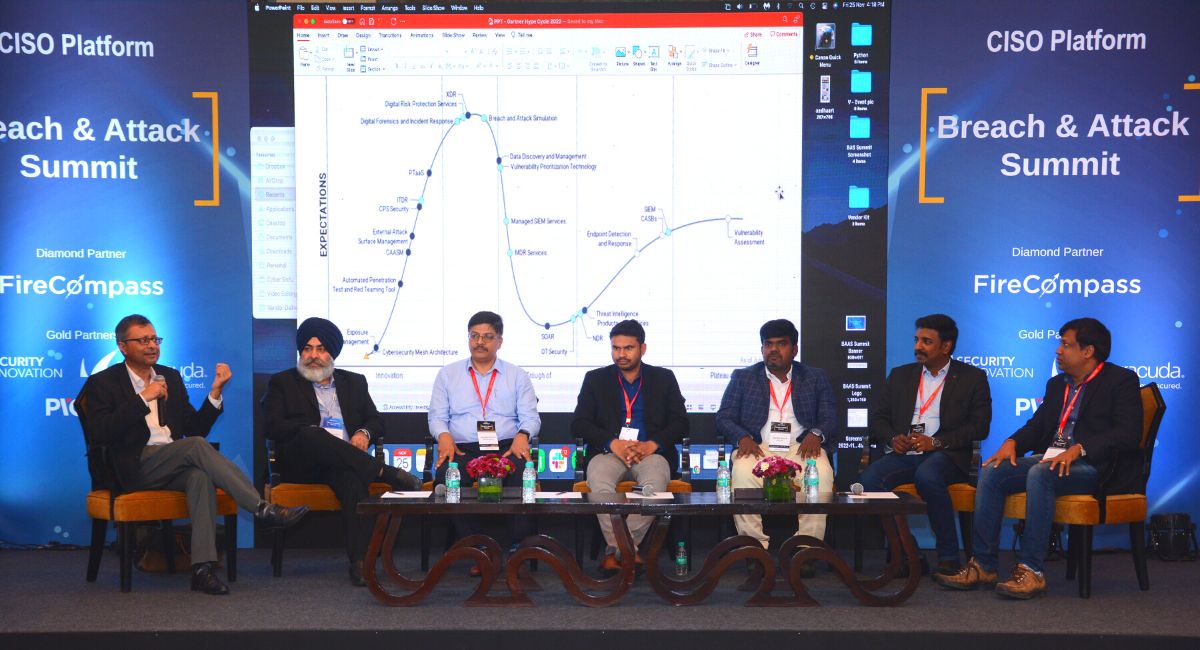
We did 3 panel discussions in 3 cities, engaging over 25+ CISOs on the Gartner Hype Cycle for Security Operations that is used by CISOs to identify the hype and expectations and insight into what technologies and trends are likely to become more important in the near future.
Panel Speakers
- Somshubhro Pal Choudhury, Partner, Bharat Innovation Fund
- R Nantha Ram, Leader - Cyber Security Operation, 3M TCOE
- Naseem Halder, CISO, ACKO General Insurance Ltd
- Nitish Goyal, Director, Ocwen Financial Services
- Philip Varughese, Global Head - Applied Intelligence, Platforms and Engineering, DXC Security
- Sandeep Bansal, Head ICT, Reva University
- Harmeet Kalra, Regional Sales Director (India & SAARC), Picus
Discussion Highlights
1. From the Gartner Hype Cycle- Pick 1-2 areas you are personally excited about… what you think is the need of the hour
Here are the top emerging technologies picked by CISOs:
- External Attack Surface Management
- Exposure Management
- Automated Penetration Test & Red Teaming
- PTaaS
- Digital Risk Protection Services
- XDR
2. What's your focus on the new entrants and its importance in the near future
The new hyped entrants are Exposure Management, External Attack Surface Management and Automated Penetration Test & Red Teaming… XDR (which in a way is a better EDR and was already there).
- Exposure Management: It is important to note that exposure management should be approached as a comprehensive program and not just the use of a single tool. This includes conducting activities such as identifying the likelihood of exploitation based on visibility into the attack surface, inventorying and categorizing exposure in terms of vulnerabilities, threat intelligence, and digital assets, and validating the effectiveness of security controls in detecting or preventing potential attacks.
As Gartner recommends, “Expand to a broader exposure management to include unpatchable attack surfaces and assess the need for solutions, such as digital risk protection services (DRPS), external attack surface management (EASM) and/or security rating services (SRS) for coverage of other exposure points, such as supply chain and shadow IT in the cloud”.
- External Attack Surface Management: The evolution of External Attack Surface Management EASM has been driven by the need to stay ahead of the constantly changing attack surface and learning what is being exposed to the hackers. As Gartner defines it, EASM describes a set of products that help organizations in identifying risks coming from internet-exposed assets that may be unknown to the organization and may contain unknown vulnerabilities. EASM is seen to be expanding into aspects of BAS, digital risk protection services (DRPS), and Security Rating Services (SRS). As a CISO said, “EASM solution has the ability to automatically identify risks in subsidiary companies and affiliated entities, whereas traditional security measures such as VA,PT and BAS can only detect such risks if we have prior knowledge of these environments and have deployed the system in those locations.
- Automated Penetration Test & Red Teaming : One of the key ways that Automated Penetration Test & Red Teaming has evolved is through the use of AI and machine learning. Through automation, it can run a large number of emulated attacks through playbooks in a short period of time, allowing organizations to identify their security risk posture. Additionally, it reduces false positives and focuses on the most critical vulnerabilities that might be attacked first. As a CISO said, “Automated Red Teaming adds value by eliminating repetitive manual tasks and significantly increasing the speed and scope of the testing.”
- XDR (Extended Detection and Response): is a security solution that aims to provide a more comprehensive and integrated approach to threat detection and response than traditional EDR (Endpoint Detection and Response) solutions. It typically includes the capabilities of EDR and also integrates data from other sources such as network and cloud to provide a more complete view of the threat landscape, enabling more effective detection and response to security incidents. Some experts believe that XDR is a better solution than EDR as it provides a more holistic approach to threat management. As a CISO, “it is my belief that XDR (Extended Detection and Response) is a more effective solution than traditional EDR (Endpoint Detection and Response)”.
3. What CISOs should keep in mind while adopting disruptive cyber security technologies ?
Several points were mentioned by CISOs and here are some key considerations:
- Scalability: The technology should be able to scale to meet the organization's future needs
- Continuous monitoring: CISOs should continuously monitor the technology for any issues or vulnerabilities and have a plan for incident response
- Compliance & Governance: The technology should comply with any relevant regulations and industry standards. CISOs should ensure that the new technology aligns with the organization's overall governance and compliance policies
- Automation: products can be leveraged to improve the efficiency and effectiveness of security processes, and can free up resources to focus on more strategic initiatives. Automation can also help to reduce the risk of human error and improve the speed of incident response
- Integration: The technology should be able to integrate with existing systems and processes within the organization
- Risk Management: CISOs should assess the risks associated with the adoption of new technology, and have a plan in place to manage those risks
- Staffing: Adequate staff and resources should be in place to support the new technology, including training and support for end-users
- Business Impact: The new technology should align with the organization's business goals and objectives
- Continuous improvement: CISOs should view the adoption of disruptive technologies as an opportunity to continuously improve and adapt the organization's security posture, and not as a one-time event


Comments