Mass Cryptojacking Campaign Targeting 3,500+ Websites
Source: TheHackerNews
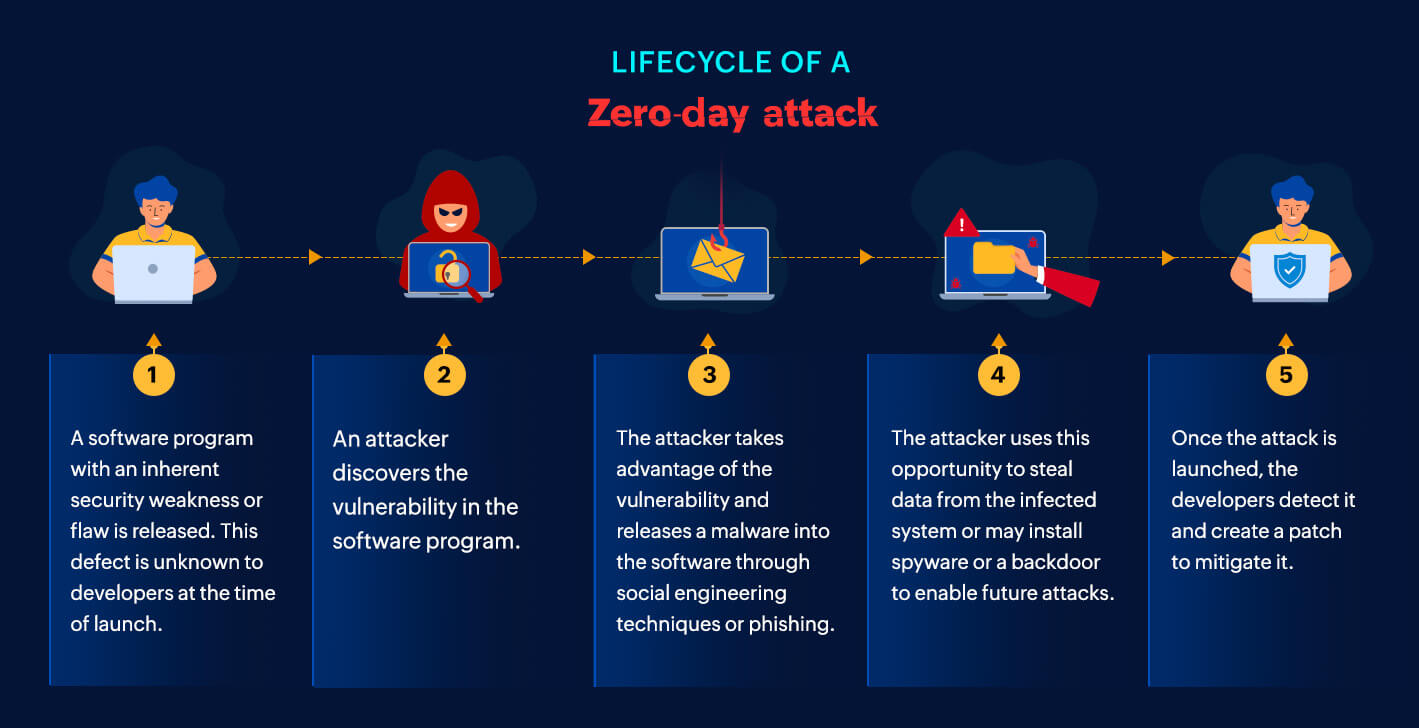
• July 21, 2025: Security researchers discover widespread JavaScript-based cryptomining campaign
• Ongoing: Dynamic payload delivery via WebSocket connections
Indicators of Compromise (IOCs):
- Obfuscated JavaScript miners in website source code
- WebSocket connections to cryptomining pools
- Background Web Worker processes consuming CPU cycles
- Dynamic thread adjustment based on system monitoring
Analysis: This campaign demonstrates evolution in cryptojacking methodologies with advanced evasion capabilities. The use of WebSocket protocols for dynamic payload delivery and resource-aware mining optimization indicates sophisticated threat actor capabilities. Organizations should implement enhanced web application security monitoring and client-side protection mechanisms.

Comments