Multi-cloud? What it really means? Is it really another approach towards risk segregation towards ensuring resilient IT infrastructure? We have seen a lot over last few decade. How IT evolved and we realised that enough is not enough. And indeed, da
Blog (927)
Thanks to DynamicCISO for a great discussion about the changing landscape of cybersecurity and how we must all adapt to drive trust into the global digital ecosystem. The key to our success is to think ahead and show leadership in managing innovation
CISO burnout is a serious issue and through this discussion, we try to find out the impact of this issue on organizations and individuals. The CISO role is operation intensive and gruelling. In most cases CISOs remain in an organisation for about 1 t
Happy Privacy Day to all those privacy professionals out there that work to make our digital world more safe, respectful, and private.
Now more than ever, respecting privacy in our rapidly digitizing world, is important. Over the past many years, pri
Norton recently announced its Anti-Virus product will have a new feature that enables mining of Ethereum cryptocurrency for their customers, if they choose to participate. Is this a nice benefit for users or a reckless move to that increases overall
Ransomware is a growing scourge. Is it possible to eradicate this entire class of attacks? I think it is but in today’s Cybersecurity Insights interview I have a lively debate with Malcolm Harkins on criminalizing ransomware payments and different ap
Technology can be mesmerizing. We are all lured by the seemingly endlessly tantalizing stream of emerging technologies that promise to connect and enrich our lives. But there is a potential dark side. For every great innovative benefit, there are acc
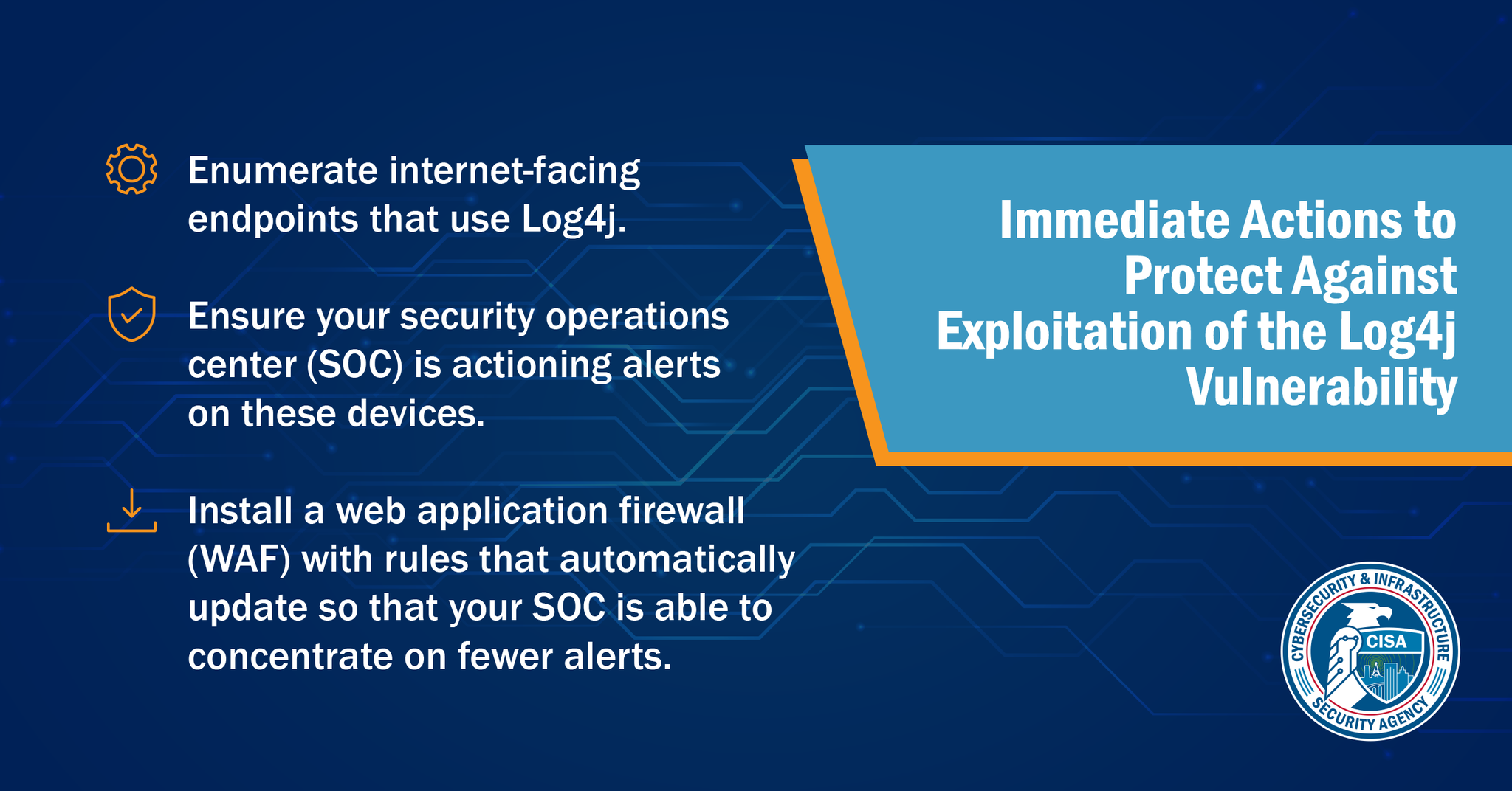
We're talking about the latest Java-based vulnerability CVE-2021-44228. Recently, a critical Zero-day vulnerability has been found in log4j which permits Remote Code Execution (RCE) allowing the attackers to get remote access. The Vulnerability got
New Fixes Added for CVE-2021-45046, CVE-2021-45105
Background on Apache log4j 2
Apache log4j 2 is an open source Java-based logging framework, which is leveraged within numerous Java applications around the world. Compared with the original log4j 1.X r
CISO Contributors
- Rajiv Nandwani (IT Security & physical security continuity senior manager, BCG)
- Vijay Kumar Verma (SVP & Head Cyber Security Engineering, Jio Platforms)
- Vikas kapoor (Vice President, Cyber Security, VOIS)
Panel Discussion (Rec
CISO Platform
A global community of 5K+ Senior IT Security executives and 40K+ subscribers with the vision of meaningful collaboration, knowledge, and intelligence sharing to fight the growing cyber security threats.
Join CISO Community Share Your Knowledge (Post A Blog)
Atlanta Chapter Meet: Build the Pen Test Maturity Model (Virtual Session)
- Description:
The Atlanta Pen Test Chapter has officially begun and is now actively underway.
Atlanta CISOs and security teams have kicked off Pen Test Chapter #1 (Virtual), an ongoing working series focused on drafting Pen Test Maturity Model v0.1, designed for an intel-led, exploit-validated, and AI-assisted security reality. The chapter was announced at …
- Created by: Biswajit Banerjee
- Tags: ciso, pen testing, red team, security leadership