Welcome to a Interesting Fireside Chat where Brad La Porte, former Gartner Analyst, and Bikash Barai, Co-Founder of FireCompass, delve deep into the world of Continuous Security Validation & Testing. In this discussion, we'll explore how Cybercrime has become an underground economy, the importance of continuous security validation, and what it means for the ever-changing threat landscape.
About Speaker
Brad LaPorte has been on the frontlines fighting cyber criminals and advising top CEOs, CISOs, CIOs, CxOs and other thought leaders on how to be as efficient and effective as possible. This was conducted in various advisory roles at the highest levels of top intelligence agencies, as a Senior Product Leader at both Dell and IBM, at multiple startups, and as a top Gartner Analyst.
Bikash Barai is the Co-Founder of FireCompass, known for his innovations in Network Security and Anti-Spam Technologies with multiple USPTO patents. He's been recognized by Fortune in their Top 40 Business Leaders under 40 list in India and is a prominent speaker at events like TiE, RSA Conference USA, and TEDx.
Fireside Chat (Recorded)
The Cybercrime Has Become An Underground Economy
Brad La Porte, with over two decades in the cybersecurity industry, brings a unique perspective on the field's evolution. From his military days to consulting with High Tide Advisors, Brad has witnessed a monumental shift. The days of manual, 'men in black' forensics tools have given way to a high-tech battleground. The arsenal of attackers has grown, harnessing cloud-based tools, machine learning, and artificial intelligence.
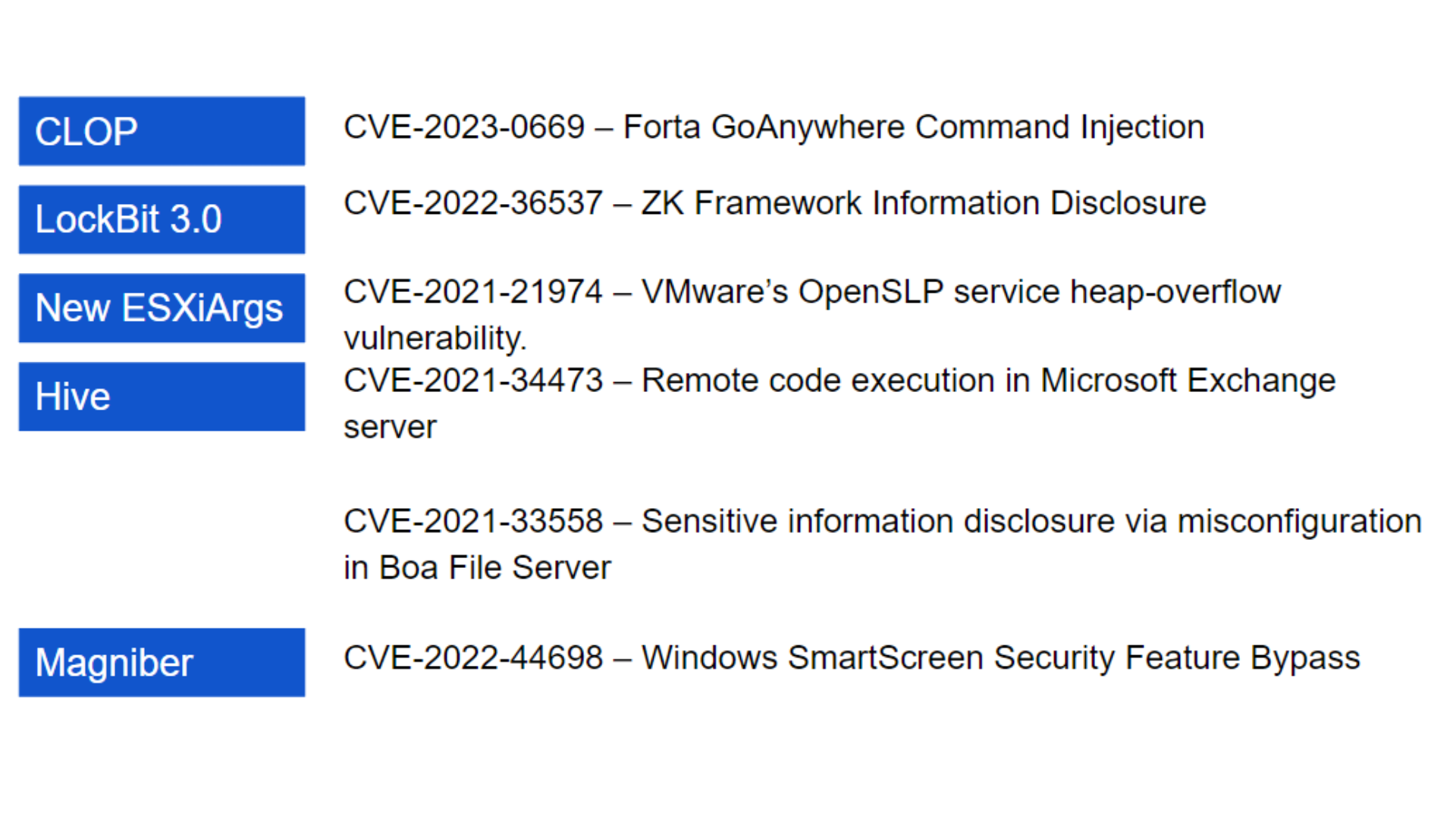
This digital transformation isn't exclusive to defenders; criminals have adopted these technologies too. Cybercrime has become an underground economy, where you can outsource malicious activities with a few clicks. Ransomware as a service, supply chain breaches, and other cyber threats are just a Bitcoin away.
The Rise Of Continuous Security Validation
Continuous Security Validation is the response to this ever-growing menace. Organizations have become more serious about security, driven by the fear of being on the front page of a newspaper for the wrong reasons. The cost of a breach goes beyond immediate losses; it affects brand reputation and long-term security posture.
This evolution demands a change in mindset. Accepting that breaches will happen, and being proactive about security is paramount. The 'not in my backyard' mentality is changing, but it's not pervasive enough. It's not a matter of 'if' a breach will occur, but 'when' and 'how bad.' Organizations need to be in a continuous state of readiness, battling breaches on multiple fronts.
The State Of The Industry
The Agile Adversary
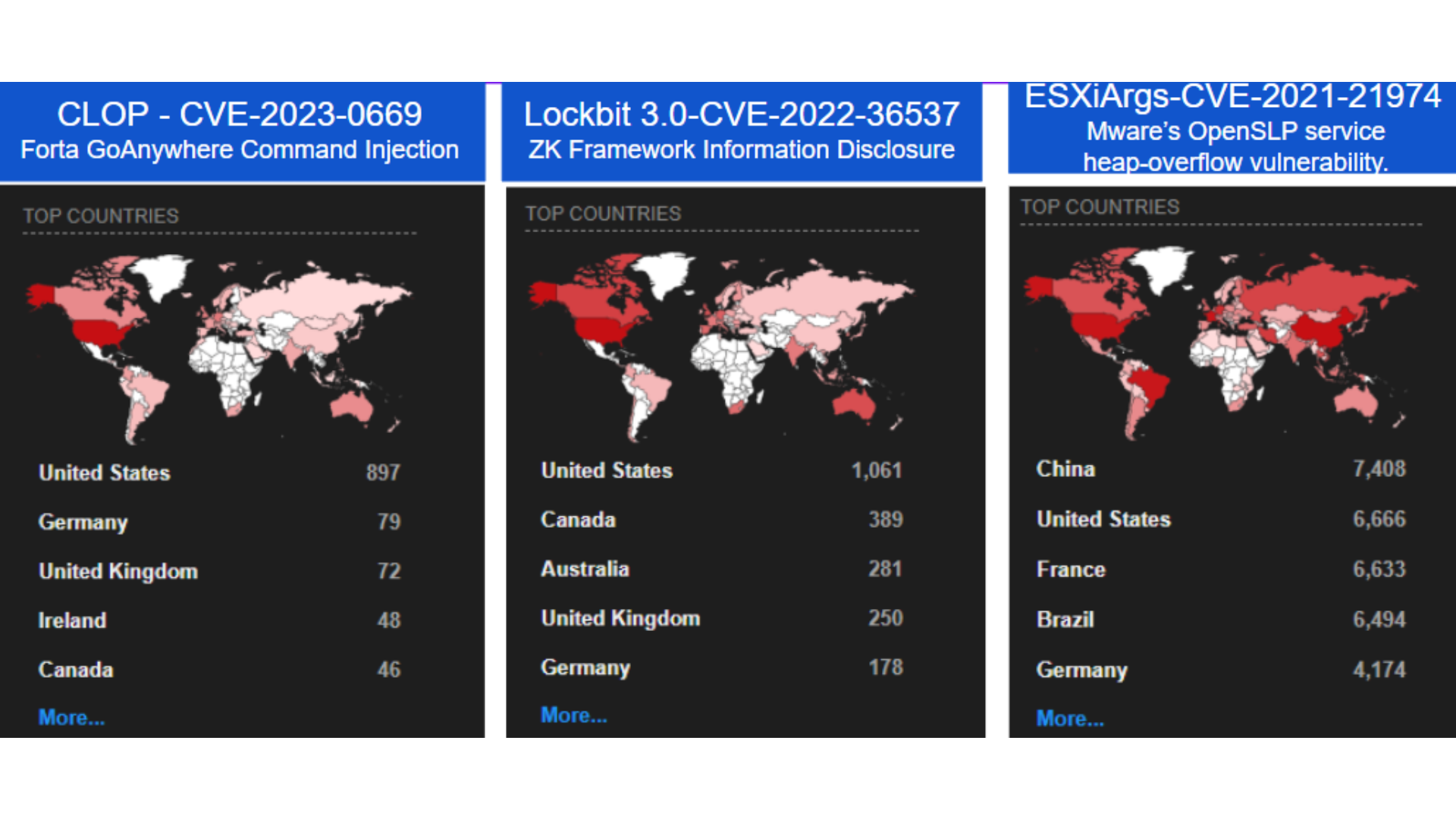
The adversary landscape has transformed into something agile. Just like developers, attackers make continuous changes. They seek windows of opportunity, and when they find them, they strike. This dynamic environment necessitates continuous testing and validation of security measures.
Simple Breaches, Huge Consequence
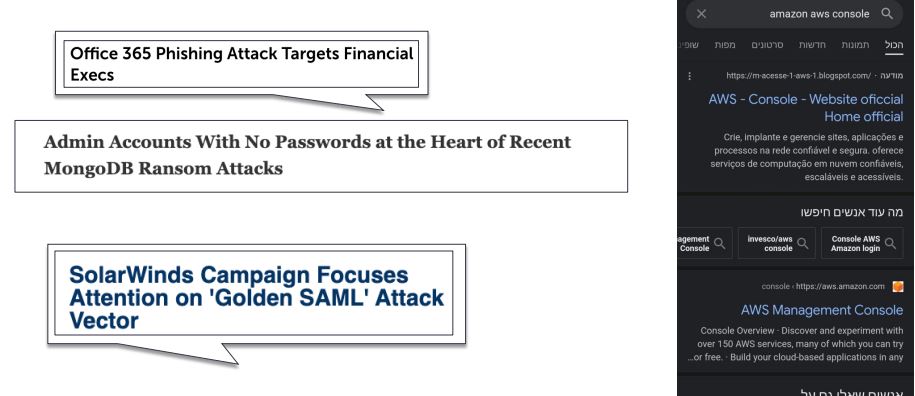
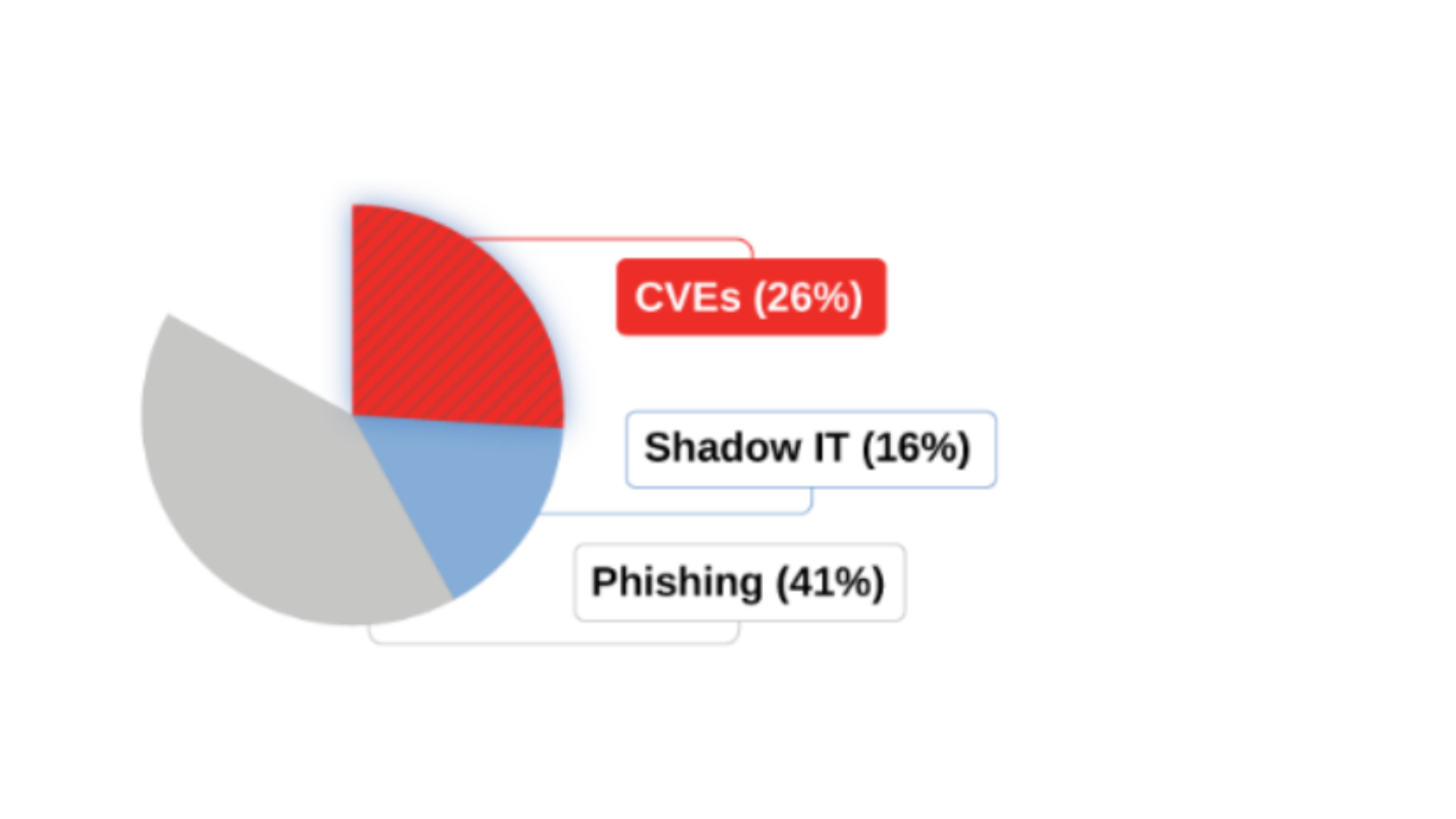
Many breaches appear deceptively simple, reminiscent of the 'For want of a nail' poem. Small misconfigurations can lead to massive compromises. Although zero-day vulnerabilities are powerful, they're rare culprits. Most breaches occur due to easily exploitable weaknesses.
The Way Forward
For CISOs, CIOs, Cyber Security Managers, Vulnerability Managers, and Security Analysts, understanding these dynamics is essential. Continuous Security Validation is not an option but a necessity in this evolving landscape. To ensure your organization's safety, you must adopt a proactive, continuous testing approach.
Embrace Continuous Security
The number one piece of advice is to fully embrace continuous security validation horizontally and vertically across your organization. Accept that breaches are inevitable, and focus on 'when' rather than 'if.' This mindset shift is crucial.
Join CISO Platform
To stay updated on the latest in cybersecurity and connect with like-minded professionals, consider joining CISO Platform, the CyberSecurity Community. Access valuable insights, discussions, and resources to fortify your organization's security posture.
Join CISO Platform - the CyberSecurity Community: Sign Up Now
>>> Part 2 Of Continuous Security Validation by Brad La Porte & Bikash Barai
.png?profile=RESIZE_710x)