This is smart: a financial sector CISO recognizes the inherent risks of MCPs, that are used by agentic AIs, and role-plays the attackers to find vulnerabilities to protect the overall environment! Focusing red and purple team investments to areas tha
vulnerability (31)
2026 will be a transformational year for cybersecurity, fueled by Artificial Intelligence.
This is the full Top 10 Cybersecurity Predictions video. By the end, you will see how the maneuvering of the threat agents will win by exploiting the capabiliti
The unfortunate truth is that poorly designed and improperly secured Artificial Intelligence integrations can be misused or exploited by adversaries, to the detriment of companies and users. Some of the compromises will bypass the traditional cyberse
Managing cyber risks and system vulnerabilities in the face of rising threats, is becoming more challenging.
Join me and Robert Leong, Senior Director of Product Management, HCL BigFix at HCLSoftware, for an exclusive Cybersecurity Leadership roundtab
The first malicious Model Context Protocol (MCP) server has been discovered and we should all be worried how this is foreshadowing AI cybersecurity risks!
Cybersecurity researchers at Koi Security detected malicious code within an MCP server that conn
Microsoft faces ongoing, systemic cybersecurity failures rooted in blind spots within its very organizational design. These vulnerabilities repeatedly result in serious product blunders and damaging breaches. This has once again become evident with t
I am very glad that the Common Vulnerabilities and Exposures (CVE) program was re-funded by the US Government, specifically CISA (Cybersecurity and Infrastructure Security Agency), but this last-minute catch has raised serious concerns with the recen
The recent undocumented code in the ESP32 microchip, made by Chinese manufacturer Espressif Systems, is used in over 1 billion devices and could represent a cybersecurity risk. Its reveal by security researchers has kicked off an interesting discussi
For over a decade, we warned the healthcare industry this was coming. They ignored us. Their sole focus was HIPAA compliance — checking regulatory boxes rather than securing critical systems. We told them that system and service availability attacks
Microsoft has stumbled yet again. Its Recall feature — intended to enhance user experience by periodically capturing screenshots — has become a glaring example of how well-intentioned technology can undermine security and privacy.
Does this sound fami
A “Perfect” 10 vulnerability score is not what users of Cisco Ultra-Reliable Wireless Backhaul (URWB) systems were expecting. The recently discovered cybersecurity vulnerability CVE-2024–20418 is remote, easy, and gives full Admin rights to the devi
I had a great discussion on the SECURITYbreak podcast talking about security vulnerability research impacting Apple vision pro VR headsets, MasterCard’s acquisition of threat intelligence vendor Recorded Future, and some horrific aspects of cybercrim
When cybersecurity researchers break the law, destroy their reputation, and make the bug-bounty research community look bad.
TL:DR Researchers found a vulnerability in a cryptocurrency exchange. They notified the company, but then exploited the bug to
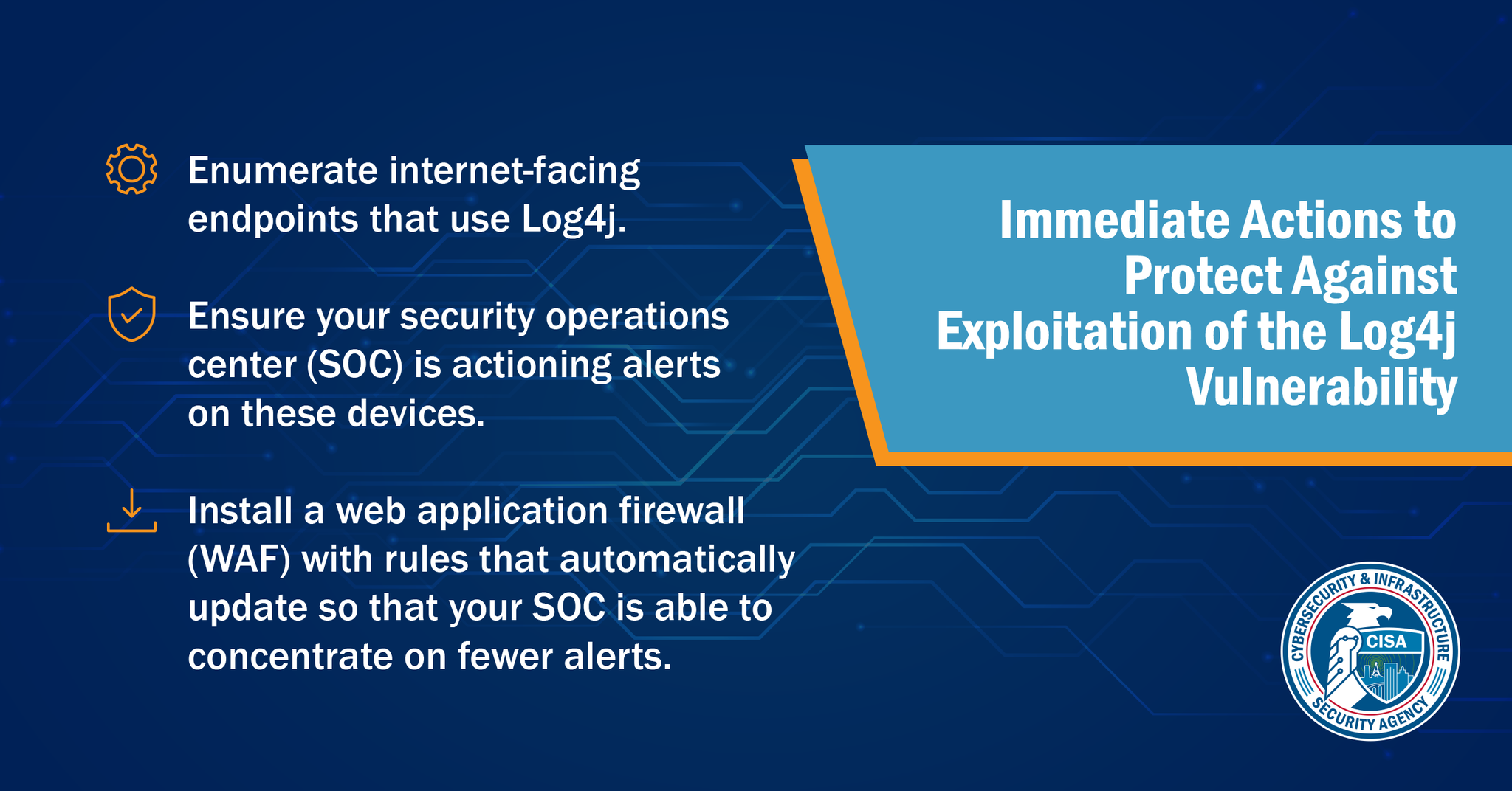
We're talking about the latest Java-based vulnerability CVE-2021-44228. Recently, a critical Zero-day vulnerability has been found in log4j which permits Remote Code Execution (RCE) allowing the attackers to get remote access. The Vulnerability got
 Recently, we were pentesting a Data mining and Analytics company. The amount of data that they talked about is phenomenal and they are planning to move to Big Data. They invited me to write a blog on state of the art, Big Data security concerns and c
Recently, we were pentesting a Data mining and Analytics company. The amount of data that they talked about is phenomenal and they are planning to move to Big Data. They invited me to write a blog on state of the art, Big Data security concerns and c
Our editorial team has handpicked some great talks from Black Hat Conference - one of the largest IT Security Conference in the world.
Black Hat - built by and for the global InfoSec community - returns to Las Vegas for its 19th year. This six day e
Overview
With the increasing need of Bluetooth Low Energy (BLE) IoT security, comes the part of vulnerability management in these networks. Unlike the IP security, BLE security framework is not yet mature. The newer version of BLE have enhanced the s
Many new devices are trying to fit into our life seamlessly. As a result, there’s a quest for a “universal access methods” for all devices. Voice activation seems to be a natural candidate for the task and many implementations for it surfaced in rece
Background:
It has been suggested that any new development will include less than 1% original code. If this isn’t presently true, it will likely be as time progresses.
With any security program, the goal is to identify the vulnerabilities, the relate
CISO Platform
A global community of 5K+ Senior IT Security executives and 40K+ subscribers with the vision of meaningful collaboration, knowledge, and intelligence sharing to fight the growing cyber security threats.
Join CISO Community Share Your Knowledge (Post A Blog)
Atlanta Chapter Meet: Build the Pen Test Maturity Model (Virtual Session)
- Description:
The Atlanta Pen Test Chapter has officially begun and is now actively underway.
Atlanta CISOs and security teams have kicked off Pen Test Chapter #1 (Virtual), an ongoing working series focused on drafting Pen Test Maturity Model v0.1, designed for an intel-led, exploit-validated, and AI-assisted security reality. The chapter was announced at …
- Created by: Biswajit Banerjee
- Tags: ciso, pen testing, red team, security leadership