Learn About Top Breches, Attack Trends & Techniques And How To Defend Against Them. Our editorial team has handpicked the top sessions at Breach & Attack Summit held in Bangalore, Mumbai and Chennai. Here are the list of top sessions in Breach & Attack Summit 2022.
350+ CISOs & Members joined us, 80+ Speakers shared their knowledge with the community and 47K+ engaged on social media. Attendees experienced keynotes, panel discussions and hands on workshops.

1 - (Keynote) Dissecting Verizon DBIR: What's Causing Most Breaches?
Speaker: Jitendra Chauhan
Analysis Of Verizon DBIR & Top Attack Vectors. The cyber security world has been very active last year - from very well-publicized critical infrastructure attacks to massive supply chain breaches. In this event, we will look deep into Verisign DIBR report and find out how attackers navigate to your valuable assets and what you can do about it.
>> Go To Presentation

2 - (Keynote) Shift Left Of Boom: The new "Shift-Left" Movement That CISOs Must Keep An Eye On
Speaker: Sachin Deodhar
At its core, “boom” is an unwanted, bad event for the defender — the initial contact from the offender. “Left of boom” is the set of events that occur in the timeline before the boom and “right of boom” is the set of events that follows. If we applied this to the cyber domain, Left of Boom would refer to those proactive initiatives and actions that are designed to prevent/preempt (or minimize risk associated with) an adverse cyber event.
>> Go To Presentation

3 - (Keynote Panel) Building A Reference Architecture For Detect, Respond And Recover Capability
Moderator: Sanil Anad Nadkami
Panel: Aditi Lath, Manikant R Singh, Dheemanth R, Rajesh Jain, Satya Maddela, Senthil N, Vikash Kumar Singh, Purna Reddy Bolla, Anshuman Singh

4 - (Workshop) Practical Approaches For Securing IoT Ecosystems
Speaker: Maithri Nadig, Rahul U, Krishnaa Srinivasa

5 - (Keynote Panel) Strategies To Manage The Unknown Unknowns In Your Attack Surface
Moderator: Navaneethan M,
Panel: Yogesh M, Manoj Kuruvanthody, Samrat Bhatt, Satya NM, Shaik Javeed Ahmed, Srinivas Thimmaiah, Arnab Chattopadhayay

6 - (Workshop) Purple Teaming With Adversary Emulation
Speaker: Sachin Deodhar
Adversary emulation involves leveraging your Red Teams to use real world adversary tactics, techniques and procedures (TTPs), alongside attack frameworks such as MITRE ATT&CK to: Identify control gaps (and weaknesses); Validate your monitoring, detection and response capabilities; Prioritizing your security investments towards mitigating any shortcoming that may be observed using this approach.
>> Go To Presentation

7 - CISO Platform Task Force Initiative 2022
Speaker: Bikash Barai
A global community of 5K+ Senior IT Security executives and 40K+ subscribers with the vision of meaningful collaboration, knowledge, and intelligence sharing to fight the growing cyber security threats.

8 - (Keynote Panel) Managing Security During Turbulent Times
Moderator: Roshan Williams
Panel: Prathap R, Raghavendra Bhat, Satish Kumar Dwibhashi, Shetty KV, Vishal Kalro, Murali Krishnaam, Aditya Kakrania
.jpg?profile=RESIZE_710x)
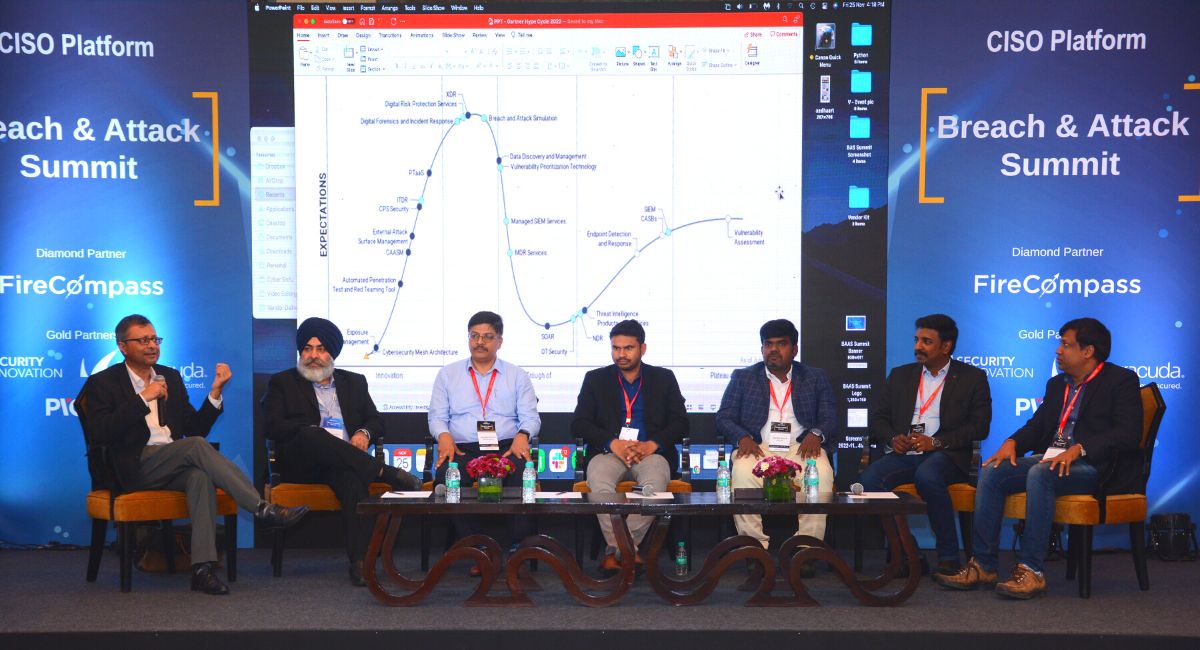
9 - (Keynote Panel) Analysing Recent Gartner Hype Cycle And Emerging New Technologies
Moderator: Somshubhro Pal Choudhury
Panel: Asif Nalakath, Nantha Ram, Naseem Halder, Nitish Goyal, Philip Varughese, Sandeep Bansal, Anirudha Nayak, Harmeet Kalra
10 - (Workshop) Decoding CIS Risk Assesment Method V2.1 : How To Leverage
Speaker: Aditya Kakrania
Risk assessments are valuable tools for understanding the threats enterprises face, allowing them to organize a strategy and build better resiliency and business continuity, all before a disaster occurs. Preparation is key – after all, the worst time to plan for a disaster is during a disaster.
>> Go To Presentation
.jpg?profile=RESIZE_710x)
11 - (Keynote Panel) Building A Reference Architecture For Detect, Respond And Recover Capability
Moderator: Bijender Kumar Mishra
Panel: Urvish Acharya, Tejas Shah, Pradipta Patro, Suresh A Shan, Vasudevan Nair, Satyanandan Atyam, Anshuman Singh

12 - (Keynote Panel) Analysing Recent Gartner Hype Cycle And Emerging New Technologies
Moderator: Vijay Kumar Verma
Panel: Hiren Pandey, Shitij Bhatia, Sanjay Jaiswal, Rohit Yeshwant Rane, Satyavrat Mishra, Melwyn Rebeiro, Harmeet Kalra

13 - (Keynote Panel) Managing Security During Turbulent Times
Moderator: Ambarish Kumar Singh
Panel: Balram Choudhary, Dr. Naresh Kumar Harale, Shankar Jadhav, Shobhana Lele, Venkata Satish Guttula, Satyanandan Atyam, Aditya Kakrania

14 - (Keynote Panel) Managing Stress During Crisis
Moderator: Bikash Barai
Speaker: Ajay, Harshad Mengle, Mohd Imran
.jpg?profile=RESIZE_710x)
15 - (Keynote Panel) Strategies To Manage The Unknown Unknowns In Your Attack Surface
Moderator: Dilip Panjwani
Speaker: Kedar Telavane, Sachin Kawalkar, Gopal Gupta, Kalpesh Doshi, Ananth MS

16 - (Keynote Panel) Building A Reference Architecture For Detect, Respond And Recover Capability
Moderator: Gowdhaman Jothilingam
Panel: Prabhakar Ramakrishnan, Venugopal Parameswaran, M Sivasubramanian, Srinivasulu Thayam, Maharajan S, Anshuman Singh

17 - (Keynote Panel) Strategies To Manage The Unknown Unknowns In Your Attack Surface
Moderator: Vijaykumar Radhakrishnan
Panel: Vijayakumar KM, Lakshmi Narasimhan R, Venkatasubramanian Ramakrishnan, Palanikumar Arumugam, Vijay Anand, Gokulavan Jayaraman, Thamaraiselvan, Arnab Chattopadhayay
.jpg?profile=RESIZE_710x)
18 - (Workshop) Purple Teaming With Adversary Emulation
Speaker: Jitendra Chauhan
Adversary emulation involves leveraging your Red Teams to use real world adversary tactics, techniques and procedures (TTPs), alongside attack frameworks such as MITRE ATT&CK to: Identify control gaps (and weaknesses); Validate your monitoring, detection and response capabilities; Prioritizing your security investments towards mitigating any shortcoming that may be observed using this approach.
>> Go To Presentation
.jpg?profile=RESIZE_710x)
19 - (Keynote Panel) Chennai Chapter Presentation
Panel: Gokulavan Jayaraman, Prabhakar Ramakrishnan, Thamaraiselvan S, Suprakash Guha, Gowdhaman Jothilingam, Srinivasulu Thayam

20 - (Keynote) Shift Left Of Boom: The New "Shift-Left" Movement That CISOs Must Keep An Eye On
Speaker: Arnab Chattopadhayay
At its core, “boom” is an unwanted, bad event for the defender — the initial contact from the offender. “Left of boom” is the set of events that occur in the timeline before the boom and “right of boom” is the set of events that follows. If we applied this to the cyber domain, Left of Boom would refer to those proactive initiatives and actions that are designed to prevent/preempt (or minimize risk associated with) an adverse cyber event.
>> Go To Presentation
.jpg?profile=RESIZE_710x)
21 - (Keynote Panel) Analysing Recent Gartner Hype Cycle And Emerging New Technologies
Moderator: AVS Prabhakar
Panel: Balakrishnan Kanniah, Gopi Krishna Togarcheti, Madhavan GG, Kavitha Srinivasulu, Suprakash Guha, Srinivasan

/Banner%20with%20partner%20logo.png)
/Speakers.png)
.png?profile=RESIZE_710x)


















.jpg?profile=RESIZE_710x)

.jpg?profile=RESIZE_710x)



.jpg?profile=RESIZE_710x)


.jpg?profile=RESIZE_710x)
.jpg?profile=RESIZE_710x)

.jpg?profile=RESIZE_710x)


